1.
Introduction ^
In Germany computerized solutions for elections were first deployed in 1999. Voting machines produced by the company Nedap1 were sporadically used on several election levels just like for the federal elections in 2005. Although a positive evaluation was given by the Physikalisch Technische Bundesanstalt and a type approval was granted by the Federal Ministry of the Interior, their use was criticized. It was reported that machines of another instruction type are prone to eavesdropping of electromagnetic emanations and a group of hackers demonstrated how to use these machines to play chess2. After the federal elections in 2005, two complaints requesting the scrutiny of the election were submitted to the Federal Constitutional Court. They were well founded because the voting machines did not meet the requirements made by the constitution. After the judgement from 3rd March, 2009 it must be possible for citizens to check the essential steps in the election act and the ascertainment of the results reliably and without special expert knowledge3. The verdict was followed by a lively discussion about the «new» requirements for eVoting machines. However, the deployment of this technology may not only take the hurdling of the public nature of elections. It also needs to be assured that the principle of the secret suffrage is not violated. This means that no one else than the particular voter may take knowledge of the respective voting decision to preserve voter privacy. For several eVoting systems the principle of the secret suffrage has been well evaluated. However, this is made on the basis of technical criteria and to our knowledge a legal analysis has not been conducted. The goal of this article is to summarize weaknesses of current eVoting systems and to evaluate which vulnerability prevents a system from being used for German parliamentary elections. We focus on German law because the verdict of the Federal Constitutional Court set new standards concerning the deployment of eVoting systems and posed new questions regarding all electoral principles. On the basis of this analysis future work regarding privacy-enhancing technologies can be identified which will be applicable for legal regulations of other countries as well. This article focuses on weaknesses of eVoting systems proposed for poll-site voting because here the voter still uses a secret polling booth and the eligibility is controlled by poll workers. Insofar, eVoting machines (e.g. the machines produced by Smartmatic) like Direct Recording Electronic voting machines (DRE) with Voter Verifiable Paper Audit Trails (VVPAT) and scanning solutions are viewed. Further we consider end-to-end verifiable eVoting systems like Prêt à Voter4 and Scantegrity5. Nevertheless, a couple of weaknesses and the corresponding legal examination can be transferred to remote voting systems as well. Generally, this article does not discuss privacy problems specific to one system like for instance the invisible ink used for Scantegrity. Therefore prior to the assignment of a certain eVoting system further evaluation is needed (regarding all electoral principles).
2.
Voter Privacy ^
2.1.
Possible Violation Caused by Hardware Modules ^
Printer knowledge: Some end-to-end verifiable voting systems propose the use of an adapted ballot paper which offers voters the possibility to generate a receipt during the vote casting process. This receipt can be used to check whether the vote has been recorded as cast. Using for instance the eVoting system Prêt à Voter, the ballot paper consists of two sides which can be separated by a perforation. On the left hand side the candidate names are listed in a random arbitrary order. The right hand side contains this order in encrypted and hashed form and a space against each candidate where the voters mark their vote. The human readable candidate order is detached and destroyed before voters leave the secret polling booth. Following, just the remaining encrypted candidate order and the marked positions are scanned and published (e.g. on a Web Bulletin Board (BB)). Voters receive a copy of their scanned ballot paper and as they know the secret candidate order, they can associate the marked positions with the respective candidates. Therefore, the privacy of the voter can be violated if an intruder manipulates the printer and collects the information printed on the ballot paper6. When using Prêt à Voter this means that the intruder knows the secret candidate order associated to the receipt. On the basis of the marked position the invader can reconstruct for whom the owner of the receipt cast his or her vote. This weakness could occur in eVoting systems offering a receipt, where the voting decision can be reconstructed by the use of secret information that is printed on the ballot paper.
Electromagnetic Emanations: As soon as electronic devices are used, electromagnetic radiation and sometimes even transmissions from the inside of an electronic circuit can be received and analysed7. Important for the success of this attack is the strength of compromising radiation and to what extend this information can be isolated from other signals like electronic noises8. For instance, the voting machines produced by the company Nedap have been found prone to eavesdropping9. For devices of a special construction type a signal in the radio frequency spectrum could be detected which allows conclusions regarding the cast vote. For the attack on this machine basic radio receiver equipment is sufficient and signals could be received from a distance up to 25 meter. Even if an attack is not possible to that extend electromagnetic emanation is a vulnerability of all eVoting systems making use of electronic devices.
Saving sensitive information: Many eVoting systems are designed to save votes electronically during the vote casting process. This can either be done by a DRE or by scanning the filled ballot papers. But the criterion of privacy is prone to violation if the system saves the sequential order or the instant of time for every cast vote (accidentally by poor design or on purpose by malicious codes). An adversary, who gets access to the machine and observed the polling station before, could use the knowledge about the order of votes to reconstruct particular voting decisions10. The weakness that sensitive information may be saved could occur in eVoting systems where the cast vote is recorded (in not encrypted form) in the presence of the voter.
Fingerprints: Many eVoting devices provide a touchscreen or keys as user interface and list the candidates in a fixed order (to offer identical ballot papers to all voters). In this case, fingerprints or residues can reveal information about the voting decision made by predecessors11. This is a weakness of all eVoting systems providing a machine as user interface.
Information added to printouts: Sensitive data like the instant of time when a vote is cast or the position in a sequential order can violate voter privacy. A malicious machine could generate an adapted printout containing this information by printing small dots, a modified ciphertext or an adapted barcode12. Such a manipulation would most likely remain undetected by voters and may occur in eVoting systems which record a vote and generate a printout.
Legal evaluation: All shown privacy weaknesses also violate the principle of the secret suffrage. As this requires that only voters may take knowledge of their particular voting decision, it needs to be ensured that others cannot «spy out» the decision at any time13. There are some approaches how the described attacks can be prevented. Ryan et al. for instance proposed a solution how the ballot paper can be generated in a distributed fashion to prevent that one single entity knows the association between the secret candidate order and the ciphertext printed on the ballot paper14. Regarding electromagnetic emanations it is possible to evaluate the emission prior to the election by an independent institute and implement security preventive measures according to the results. The same applies to fingerprints (prevented by a special surface), the order of cast votes and additional information on printouts (prevented by source code). In any case, additional organisational measures (like in the traditional paper based election)15 are necessary to prevent the hardware from being manipulated by intruders.
However, if voters are not able to distinguish between eVoting systems that assure the principle of the secret suffrage and those that do not, voters are not aware of violations. Insofar it is essential whether they need to be able to check the ensuring of the principle of the secret suffrage on their own. After the verdict of the Federal Constitutional Court from 3rd March, 2009 all voters must be able to check the essential steps in the election act and the ascertainment of the results. Against this background, a bundle of technical and organisational security measures (e.g. monitoring and safekeeping of the voting machines or comparability of the devices used with an officially checked sample) is not suited by itself to compensate a lack of controllability by the citizen16.
Admittedly, one section of the reasons given for the judgement gives cause for the deliberation that the claimed ability also obtains the ensuring of the electoral principles. «Only by the possibility of monitoring whether the election complies with the constitutional election principles», it is possible to ensure that the delegation of state power does not suffer from a shortcoming17. During the traditional paper based election the privacy of the voter is guaranteed because voters have to cast their vote on an official ballot paper in a secret polling booth. Meanwhile, they are able to control the inside of the polling booth by searching for holes, cameras or unwished observers. Although a full guarantee is not given, voters can check the ensuring of the principle of the secret suffrage in an applicable extent. This should be possible while using eVoting systems as well18. A total abdication on the protection of the secret suffrage is unjustifiable because in this case voters could not cast a free vote. Generally voting systems have to be produced in a way that the risks shown do not come up. But it needs to be discussed to which proportion voters should be able to control the compliance with the secret nature of elections on their own.
2.2.
Possible Violation Caused by Technical Verification ^
Assumed confidence in officials: As within the traditional voting system it has to be ensured that the privacy and functionality do not depend on one person in authority. In this context, it is inconceivable to commit the private key (for decrypting the cast votes or access information saved on a trusted device) to one official only because this person might be bribed or threatened and compromising information can be revealed (e.g. by decrypting votes before anonymisation or giving access to sensitive information). Therefore, so called threshold cryptosystems are used which require two separate keys, one public and one private, whereas the private key consists of several key portions19. In practice they could be saved on trusted devices (e.g. smartcards) and shared among several persons in authority. As a result, a predefined number of people has to be present to decrypt information or access sensitive data. Anyway, voters have to trust that the officials keep their private key secret to ensure voter privacy.
Another example for a shared responsibility is the anonymisation of cast votes. This is usually done by a mix-net, which was introduced by David Chaum in 198120. Originally this concept was proposed to allow anonymous communication within a network. In the context of eVoting, re-encryption mix-nets are used to anonymise cast votes before the decryption and tallying step to ensure voter privacy. A re-encryption mix-net consists of several «mixes» which are serially connected. The first «mix» (e.g. a server controlled by a person) takes a batch of votes, changes the appearance (by re-encrypting the secret) and shuffles the order with a secret permutation. Following the output data is passed to the next «mix» which processes the votes the same way until the whole mix-net is completed. Every «mix» knows the association between its input and output batches. Therefore, voter privacy is given only when at least one «mix» is true and keeps the used permutation secret. Summarized eVoting systems using threshold-cryptography (e.g. Prêt à Voter), using mix-nets (e.g. Prêt à Voter) or managing access to sensitive data (e.g. Scantegrity) have the drawback that voters have to trust a predefined number of officials.
Vote clustering: Assume an election is realised with DREs in polling stations. In case the machines save the votes and tally them independently it is possible to map a batch of votes to a specific DRE. This gives an additional association between a subgroup of voters and a subset of cast votes. Such a fragmentation could also occur during the verification of a mix-net (depending on the used verification method). This problem has been realised by Chaum for mix-nets verified by Randomized Partial Checking21 but a solution was proposed as well22. In general, vote clustering could occur in eVoting systems where votes are cast and tallied at several DREs, where machines sign votes or receipts, or where the votes are grouped during the verification process.
Legal evaluation: In case of using a verification method that puts voters into different blocks, the principle of the secret suffrage is concerned. Although the voting decision is not revealed, the assortment of possible candidates gets smaller23. From a legal point of view, voter privacy needs to be ensured without any reservation24. However, this does not mean that there is no margin or discretion while realising a specific voting system25. After the Federal Constitutional Court the «nature of things» entails that not every electoral principle can be fulfilled entirely26. Therefore, differentiations between the electoral principles are possible, if they are necessary because of «compulsory reasons». Reasons that allow modifications of single election principles can be bidden in the interest of the unity regarding an election system and in order to ensure the pursued political goals that comply with democratic principles. Against this background, the shown eVoting systems might be compatible with the principle of the secret suffrage if they ensured – for instance – the public nature of elections in a bigger extent.
While evaluating the capability of these systems, it must be noted that a similar situation might happen during the counting of postal votes. According to § 8.3 Federal Electoral Act the postal returning committees can be situated on local level. In view of the small number of voters it needs to be ensured that the secrecy of the vote is not put into jeopardy27. Therefore it is regulated in § 7 No. 1 Federal Electoral Code (FEC) that at least 50 voters may be allotted to one postal returning committee. The postal vote is constitutionally compatible because it does not implicate excessive constrictions of the principles of the direct, free, universal or secret suffrage28. By using postal voting, more people are able to cast their vote than it would be the case without offering this opportunity (universal suffrage). Nevertheless, the legislator is committed to care for the best safeguarding and warranting of the election principles29. Against this background, a voting system that realises the casting of votes and the verification of votes without vote clustering is preferable to one that depends on this. If vote clustering is necessary it needs to be audited whether another electoral principle is starched by this.
3.
Everlasting Privacy ^
Cryptographic codes: In general, the secrecy of encrypted information can be ensured just for a limited (and not assessable) duration of time30. It is possible at any time that the security of a cryptosystem is broken by an effective attack (e.g. engineering process or quantum computers). Further, the length of the secret keys has to be enlarged regularly due to the permanent enhancing processing power. These circumstances might enable an attacker to decrypt all encrypted published information until about some decades after the election. In the case of Prêt à Voter, for instance, an arbitrary candidate order is used and the marked positions and encrypted secret candidate order is published. As a consequence, for a specific receipt, the intruder can reveal the marked candidates if the underlying cryptosystem is broken. This temporary privacy is a drawback of all eVoting systems which use a receipt and keep the published voting decision private by using cryptography.
Legal evaluation: The question for how long a voting decision needs to remain secret is closely related to the function of the respective electoral principle. The secret suffrage does not serve a purpose out of itself. It protects the principle of the free suffrage because a free vote is not possible when voters have to fear the disclosure of their voting decision31. For this reason, the secrecy of the vote has to be ensured for an indefinite period of time. It does not draw a distinction, if voters have to reckon the disclosure of their vote tomorrow, in 20 years or in any future32.
As the receipt used for verifying the own voting decision is handed out to the voter, the information printed on it cannot be classified as private33. Although it does not reveal any provable details about the voter (e.g. name or address), the possession of it signalises to whom it belongs to. Using, for instance, the end-to-end verifiable eVoting system Scantegrity, during the vote casting process the ballot paper reveals a confirmation code for every marked candidate (the confirmation codes are printed in invisible ink and the voter uses a decoder pen). In this case everlasting privacy is fulfilled by using a «trusted device» which saves the association between the published confirmation codes and the corresponding candidate names. The vote cannot be reconstructed anymore, if this information is destroyed. Such a component could be delivered into official custody while the term of custody could be geared to the record retention periods of election documents in the traditional system. In order to realize a subsequent verification of the election outcome, ballot papers have to be kept safe until 60 days prior to the next federal elections. The state returning officer may allow the destruction earlier if they are not needed for an official proceeding (§ 90.3 FEC). Although the destruction of ballots is not compulsory according to the FEC (they can be destroyed), the obligation to do so can be discussed against the background of the constitutional principles of electoral law.
4.
Receipt-Freeness ^
Verifiable eVoting systems offer voters the possibility to revise all steps of the election regarding integrity. However, voters might be exposed to external influences such as vote-selling or coercion, if receipts are used and the receipt reveals sensitive information which allows conclusions regarding the voting decision34. Therefore receipt-freeness requires that either voters cannot create a proof of the content of their cast vote, or they are able to generate both, receipts for real (tallied) and fake (not tallied) votes indistinguishable from each other.
Legal evaluation: After the principle of the secret suffrage the voting decision needs to remain secret after the vote casting process as well35. The disclosure of it by voters themselves does not affect this requirement as long as others may not prove the truth of this statement36. Against this background, voters may not be able to produce a proof of their voting decision. Therefore, characteristics enabling the verification of the vote after the vote casting process may not be disclosed as long as the ballot paper is under the ownership of the voter (e.g. by using scratch fields).
5.
Conclusion and Future Work ^
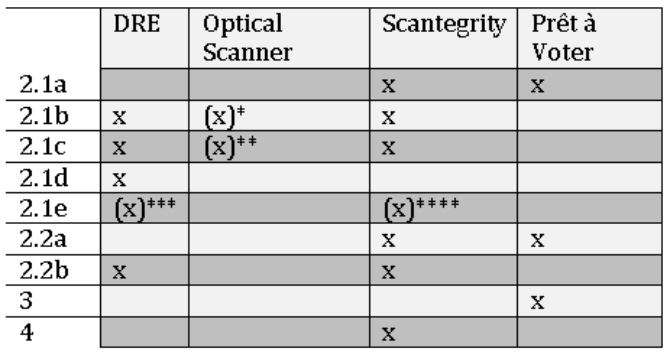
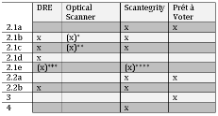
Table 5.1 gives an overview over the focused poll-site eVoting solutions and weaknesses these solutions are prone to.
Table 5.1: Table showing weaknesses of poll-site voting solutions.
* An optical scanner is vulnerable to the privacy weakness described in Section 2.1b, if the voter is present during the scanning process.
** An optical scanner is vulnerable to the privacy weakness described in Section 2.1c, if the voter is present during the scanning process.
*** DREs are vulnerable to the privacy weakness described in Section 2.1e, if a VVPAT is generated.
**** Scantegrity is vulnerable to the privacy weakness described in Section 2.1e, if a printout, containing the confirmation codes, is generated during the vote casting process.
The legal evaluation of privacy weaknesses shows where technical improvements are necessary before eVoting schemes can be used for legally binding elections. Like mentioned before, some publications already propose solutions to prevent violation of voter privacy caused by hardware modules. However, it is desirable to find privacy-enhancing technologies which are verifiable by the voter, thus they can check the compliance with the principle of the secret suffrage by themselves. The other way round it should be ensured that the verification does not reveal sensitive information which could violate voter privacy. Although many mix-net verification processes have been proposed (also focussing on preserving voter privacy), a measurement of the anonymity of the input data has not been conducted so far. As a result, it is difficult to judge whether the legal requirements are fulfilled and to determine the number of mixes needed for a predefined security level.
In addition to technical improvements, future work also concerns legal aspects. Insofar it has to be discussed if the public nature of elections applies to the essential steps of the election only or if it holds for the electoral principles as well. More precisely, it needs to be clarified whether expert-controllability is sufficient or whether voters have to be able to check the compliance of the secret nature of elections on their own. The list of open topics shows that further research is necessary – in the field of computer science, in the field of law, and in cooperation between researchers of both disciplines.
Denise Demirel is doctoral researcher at the Technische Universität Darmstadt in the Cryptography and Computer Algebra Group of Prof. Johannes Buchmann. Since November 2010 she works on the Project VerKonWa – Verfassungskonforme Umsetzung von elektronischen Wahlen (Constitutional Compliant Electronic Voting) which is funded by the Deutsche Forschungsgemeinschaft. Her Ph.D. focusses on cryptographic aspects, verifiability and (everlasting) privacy of electronic voting schemes.
Maria Henning is doctoral researcher in the «Project Group Constitutionally Compatible Technology Design» of Prof. Alexander Roßnagel at the University of Kassel. Since January 2011 she works on the Project VerKonWa – Verfassungskonforme Umsetzung von elektronischen Wahlen (Constitutional Compliant Electronic Voting) which is funded by the Deutsche Forschungsgemeinschaft. Her Ph.D. focusses on legal aspects of electronic voting and in particular on constitutionally compatible verifiability in order to fulfil the principle of the public nature of elections.
Acknowledgement: This article has been developed within the project – «VerKonWa» – Verfassungskonforme Umsetzung von elektronischen Wahlen – which is funded by the Deutsche Forschungsgemeinschaft (DFG, German Science Foundation).
- 1 Official Webpage: http://www.nedap.com/, retrieved 2. July 2012.
- 2 Http://wijvertrouwenstemcomputersniet.nl/other/es3b-en.pdf, retrieved 2. July 2012.
- 3 BVerfGE 123, 39.
- 4 Ryan, P. Y. A.; Bismark, D.; Heather, J.; Schneider, S.; Xia, Z.: Prêt à voter: a voter-verifiable voting system. In: IEEE Transactions on Information Forensics and Security, Vol. 4, 2009. IEEE Press, Piscataway, NJ, USA, 2009; pp. 662–673.
- 5 Sherman, A. T. et. al: Scantegrity III: automatic trustworthy receipts, highlighting over/under votes, and full voter verifiability. In: Proceedings of the 2011 conference on Electronic voting technology/workshop on trustworthy elections, San Francisco, CA, 2011. USENIX Association, Berkeley, CA, USA, 2011.
- 6 Discussed e.g. in Ryan, P. Y. A.; Peacock, T.: A Threat Analysis of Prêt à Voter. In: Towards Trustworthy Elections, 2010, Springer-Verlag, Berlin Heidelberg, 2010; pp. 200–215 and Xia, Z. et al.: Versatile Prêt à Voter: Handling Multiple Election Methods with a Unified Interface. In: INDOCRYPT, Hyderabad, India, 2010. Springer-Verlag, Berlin Heidelberg, 2010; pp. 98–114.
- 7 Discussed e.g. in Ryan, P. Y. A.; Peacock, T.: A Threat Analysis of Prêt à Voter. In: Towards Trustworthy Elections, 2010. Springer-Verlag, Berlin Heidelberg, 2010; pp. 200–215 and Xia, Z. et al.: Versatile Prêt à Voter: Handling Multiple Election Methods with a Unified Interface. In: INDOCRYPT, Hyderabad, India, 2010. Springer-Verlag, Berlin Heidelberg, 2010; pp. 98–114.
- 8 Http://www.hamburg.de/contentblob/260124/data/abstrahlung.pdf, retrieved 2. July 2012.
- 9 Http://wijvertrouwenstemcomputersniet.nl/images/9/91/Es3b-en.pdf, retrieved 2. July 2012.
- 10 Discussed e.g. in Keller, A. M. et al.: Privacy Issues in an Electronic Voting Machine. In: Proceedings of the ACM Workshop on Privacy in the Electronic Society (WPES), Washington, DC, USA, 2004. ACM Press, New York, NY, USA, 2004; pp. 33–34 and Pieters, W.: Combatting electoral traces: the Dutch tempest discussion and beyond. In: E-Voting and Identity: Second International Conference (VOTE-ID), Luxembourg, 2009. Springer-Verlag, Berlin Heidelberg, 2009; pp. 172–190.
- 11 Discussed e.g. in Pieters, W.: Combatting electoral traces: the Dutch tempest discussion and beyond. In: E-Voting and Identity: Second International Conference (VOTE-ID), Luxembourg, 2009. Springer-Verlag, Berlin Heidelberg, 2009; pp. 172–190.
- 12 Discussed e.g. in Karlof C.; Sastry N.; Wagner D.: Cryptographic voting protocols: A systems perspective. In: USENIX Security Symposium, Baltimore, MD, USA, 2005. Springer-Verlag, Berlin Heidelberg, 2005; pp. 33-50 and Ryan, P. Y. A.; Peacock, T.: A Threat Analysis of Prêt à Voter. In: Towards Trustworthy Elections, 2010. Springer-Verlag, Berlin Heidelberg, 2010; pp. 200–215.
- 13 Will, M.: Internetwahlen – Verfassungsrechtliche Möglichkeiten und Grenzen. Richard Boorberg Verlag, Stuttgart, 2002; p. 136.
- 14 Ryan, P. Y. A.; Peacock, T.: A Threat Analysis of Prêt à Voter. In: Towards Trustworthy Elections, 2010. Springer-Verlag, Berlin Heidelberg, 2010; pp. 200-215.
- 15 Here the secrecy of the vote is safeguarded by using secret polling booths and official ballot papers that have no connection to the particular voter.
- 16 BVerfGE 123, 39, 74.
- 17 BVerfGE 123, 39, 69.
- 18 Richter, P.: Briefwahl für alle? Die Freigabe der Fernwahl und der Grundsatz der Öffentlichkeit, DÖV 2010; p. 609.
- 19 Pedersen, T. P.: A threshold cryptosystem without a trusted party. In: Proceedings of the 10th annual international conference on Theory and application of cryptographic techniques, Brighton, UK, 1991. Springer-Verlag, Berlin Heidelberg, 1991; pp. 522–526.
- 20 Chaum, D.: Untraceable electronic mail, return addresses, and digital pseudonyms. In: Communications of the ACM, Vol. 24, 1981. ACM Press, New York, NY, USA, 1981; pp. 84–88.
- 21 Jakobsson, M.; Juels, A.; Rivest, R. L.: Making Mix Nets Robust For Electronic Voting By Randomized Partial Checking. In: Proceedings of the 11th USENIX Security Symposium, San Francisco, CA, 2002. USENIX Association, Berkeley, CA, USA, 2002; pp. 339–353.
- 22 Chaum, D.: Secret-Ballot Receipts and Transparent Integrity. Unpublished, 2002.
- 23 Imagine in a poll station two DREs are used. In that case the voters are grouped into two blocks: one block consists of the voters which cast their vote at DRE A and the other block contains the voters which used DRE B. If just one of the two DREs recorded a vote for candidate one (let’s say DRE A) and the other one did not, it is possible to say for half of the voters that they did not cast a vote for candidate one (all which cast their vote at DRE B).
- 24 Schreiber, W.: Bundeswahlgesetz Kommentar. Carl Heymanns Verlag, Köln, 2009; p. 90.
- 25 After Art. 38.3 Grundgesetz the details on voting have to be regulated by the legislator. Therefore the legislator is authorized and committed to decide in favor of a concrete voting system while protecting the constitutional principles of electoral law.
- 26 BVerfGE 59, 119, 124.
- 27 Schreiber, W.: Bundeswahlgesetz Kommentar. Carl Heymanns Verlag, Köln, 2009; p. 274.
- 28 BVerfGE 59, 119, 125.
- 29 BVerfGE 59, 119, 127.
- 30 Discussed e.g. in Moran, T.; Naor, M.: Receipt-Free Universally-Verifiable Voting with Everlasting Privacy. In: Advances in Cryptology – CRYPTO 2006, Santa Barbara, California, USA, 2006. Springer-Verlag, Berlin Heidelberg, 2006; pp.373-392 and van de Graaf, J.: Voting with unconditional privacy by merging Prêt à voter and PunchScan. In: IEEE Transactions on Information Forensics and Security, Vol. 4, 2009. IEEE Press, Piscataway, NJ, USA, 2009; pp. 674–684.
- 31 Schreiber, W.: Bundeswahlgesetz Kommentar. Carl Heymanns Verlag, Köln, 2009; p. 155.
- 32 Will, M.: Internetwahlen – Verfassungsrechtliche Möglichkeiten und Grenzen. Richard Boorberg Verlag, Stuttgart, 2002; p. 139 and Ullmann, M.; Koob, F.; Kelter, H.: Anonyme Online-Wahlen – Lösungsansätze für die Realisierung von Online-Wahlen, DuD 2001; p. 644.
- 33 An intruder might take it or the voter shows it to another person.
- 34 We do not discuss the so called Italian attack and Randomization attack because these address the principle of free suffrage.
- 35 Schreiber, W.: Bundeswahlgesetz Kommentar. Carl Heymanns Verlag, Köln, 2009; p. 156.
- 36 Morlok, M.: Artikel 38. In (Dreier, H. Hrsg.): Grundgesetz Kommentar. Mohr Siebeck, Tübingen, 2006; p. 998.