1.
Introduction ^
- Architecture descriptions have to leverage checking the compliance with the law.
- Legal informatics experts are able to contribute to legislation, especially in e-Government.
- Enterprise architects become important partners for legal informatics experts. This is possible in the revision of the law, e.g. in digital identity regulations.
- Contacts with authorities when anticipating ICT perspectives. Regulation of software exchange, e.g. modules in finance informatics.
- Ideas in legal informatics; patterns and anti-patterns.
2.
The legal perspective in legal informatics and enterprise engineering ^
- business perspective;
- ICT (information and communication technologies) perspective;
- legal perspective.
- internal communication perspective (a direction tool);
- public relations and marketing perspective;
- political and economic perspective (perhaps in e-Government).
- business level requirements (the view of business analyst);
- user level requirements (the view of stakeholders);
- IS (information system) requirements (the view of IS analyst);
- the requirements of IS subsystems (the view of IS engineer);
- software requirements (the view of software analyst).
3.
The task to be solved by a multiphase transformation ^
Phase 1. Microcontenting: from legal text to textual microcontents
Phase 2. Visualising: from textual microcontents to visualization
Phase 3. Formalising: from visualization to formalization
Phase 4. Representing: from formalization to representation in a technical language
- Writing a law to regulate the domain which involves the legal machine. This is a lawmaking task. An example is to write rules for an eGovernment application.
- Legal assessment of the law. Jurists are in the centre. The recommendations to improve both the legal machine and the law serve as the outcome.
4.
Towards a methodology of the compliance with the law ^
- Internal arrangement of transparency
- Methods for the legal architecture view as part of enterprise architecture
- Design methods for law-triggered changes in the enterprise architecture
A holistic view requires a “Governance, Risk and Compliance” 2 approach and involves three loops of management cycles [Bonazzi et al. 2009]. We think that in order to assess the IT GRC in practice, an experiment should be undertaken. An assessment according to theoretical criteria is feasible, for instance, in formal theories but is not enough in management. The reason is that the latter is a more practical rather than theoretical activity. Not all the criteria can be foreseen in advance. Each case can bring specific factors.
5.
References ^
Beck, Kent; et al. Manifesto for Agile Software Development. Agile Alliance. http://agilemanifesto.org/ retrieved 10-01-2012 (2001).
Bonazzi, Riccardo; Hussami, Lotfi; Pigneur, Yves, Compliance management is becoming a major issue in IS design. In: D'atri, Alessandro; Saccà, Domenico (eds.) Information Systems: People, Organizations, Institutions, and Technologies, Springer, pp. 391-398 (2009).
Čaplinskas, Albertas, Requirements elicitation in the context of enterprise engineering: a vision driven approach, Informatica, Lithuanian Academy of Sciences, 20(3), 343-368 (2009).
Čyras, Vytautas; Lachmayer, Friedrich, Distributive multimedia and multisensory legal machines. In: Schweighofer, E. & Kummer, F. (eds.) Europäische Projektkultur als Beitrag zur Rationalisierung des Rechts, Tagungsband des 14. Internationalen Rechtsinformatik Symposions IRIS 2011, 24.-26. Februar 2011, Universität Salzburg, Österreichische Computer Gesellschaft, Wien, pp. 567-574 (2011).
Čyras, Vytautas; Lachmayer, Friedrich, Multiphase transformation in the legal text-to-program approach. Submitted to: Izumo Takashi & Hikaru Mori (eds.) Liber amicorum Guido Tsuno. Chuo University Hachioji Tokyo, Japan (2012)
Knackstedt, Ralf; Heddier, Marcel; Becker, Jörg, Fachkonzeption Rechtskonformer Informationssysteme als Anwendungsgebiet der Rechtsvisualisierung. In: Schweighofer, E. & Kummer, F. (eds.) Europäische Projektkultur als Beitrag zur Rationalisierung des Rechts, Tagungsband des 14. Internationalen Rechtsinformatik Symposions IRIS 2011, 24.-26. Februar 2011, Universität Salzburg, Österreichische Computer Gesellschaft, Wien, pp. 549-558 (2011).
Riedl, Reinhard, Rechtsinformatik aus Sicht des Unternehmensarchitekten. In: Geist, A., Brunschwig, C. R., Lachmayer, F. & Schefbeck, G. (Hrsg.) Strukturierung der Juristischen Semantik – Structuring Legal Semantics. Festschrift für Erich Schweighofer, pp. 257-269. Editions Weblaw, Bern (2011).
Ross, Jeanne W.; Weill, Peter; Robertson, David C., Enterprise architecture as strategy: creating a foundation for business execution. Harward Business School Press, Boston (2006).
Sowa, John; Zachman, John, Extending and formalizing the framework for information systems architecture, IBM Systems Journal, 31(3), 590-616 (1992).
- 1 Submitted to Takashi, I. & Mori, H. (eds.) Liber amicorum Guido Tsuno, Chuo University Hachioji Tokyo, Japan.
- 2 See also http://en.wikipedia.org/wiki/Governance,_Risk_Management,_and_Compliance, retrieved 10-01-2012.
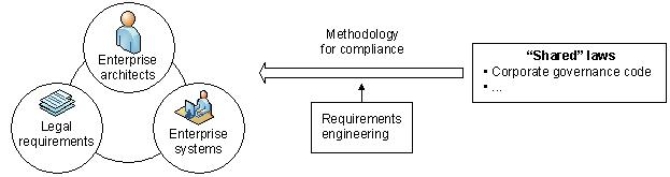
![Fig. 3: The methodological framework for requirements elicitation, analysis, specification and validation proposed in [Čaplinskas 2009, 354]](/magnoliaAuthor/dam/publicationsystem_jlit_rize/publicationsystem/articles/1/10/1055/images/1317854727.jpg)
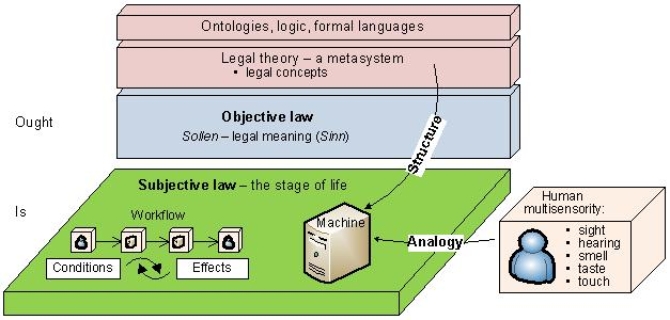
![Fig. 4: The metaphor of multibridge. Multiple transformations lead from norms in legal texts to their machine operationalization [Čyras & Lachmayer 2012]](/magnoliaAuthor/.imaging/stk/jusletterit/content/dam/publicationsystem_jlit_rize/publicationsystem/images_new/Cyras_Riedl_Abb-4/jcr:content/Cyras_Riedl_Abb.4.jpg.jpg)
![Fig. 5: Regulation and IT alignment framework; adapted from [Bonazzi et al. 2009]](/magnoliaAuthor/.imaging/stk/jusletterit/content/dam/publicationsystem_jlit_rize/publicationsystem/images_new/Cyras_Riedl_Abb-5/jcr:content/Cyras_Riedl_Abb.5.jpg.jpg)





