1.
Introduction ^
2.
Designing in Privacy and Security by Default: A proactive, POSITIVE-SUM Approach ^
The 7 Foundational Principles of Privacy by Design are as follows4:
- Proactive not Reactive; Preventative not RemedialThe Privacy by Design (PbD) approach is characterized by proactive rather than reactive measures. It anticipates and prevents privacy invasive events before they happen.
- Privacy as the DefaultPrivacy by Design seeks to deliver the maximum degree of privacy by ensuring that personal data are automatically protected in any given IT system or business practice. No action is required on the part of the individual to protect their privacy – it is built into the system, by default.
- Privacy Embedded into DesignPrivacy by Design is embedded into the design and architecture of IT systems and business practices. The result is that privacy becomes an essential component of the core functionality being delivered.
- Full Functionality – Positive-Sum, not Zero-SumPrivacy by Design seeks to accommodate all legitimate interests and objectives in a positive-sum «win-win» manner, avoiding the pretense of false dichotomies, such as privacy vs. security, demonstrating that it is possible to have both.
- End-to-End Lifecycle ProtectionPrivacy by Design, extends data security throughout the entire lifecycle of the data involved, from start to final destruction..
- Visibility and TransparencyPrivacy by Design seeks to assure all stakeholders that whatever the business practice or technology involved, it is in fact, operating according to the stated promises and objectives, subject to independent verification.
- Respect for User PrivacyPrivacy by Design requires organizations to keep the interests of the individual uppermost by offering such measures as strong privacy defaults, appropriate notice, and empowering user-friendly options.
3.
The Evolving Data Landscape: Challenges to Privacy and Security ^
Consider also the privacy and security concerns associated with Big Data.7 As technological advances improve our ability to exploit Big Data, potential privacy concerns could stir a regulatory backlash that would dampen the data economy and stifle innovation. Navigating the massive volume of information represented by Big Data requires a new and potentially innovative approach to data collection, storage, sharing and destruction. These efforts must include provisions for privacy protection. By way of example, algorithms can now automatically infer that different digital transactions in different systems are in fact related to the activity of a single person or household. A bank that wants to better serve its customers will be eager to know if a specific customer has three relationships with the bank and has an enormous Twitter following. In the past, identifying the difference between six people, each with one fact, versus one person with six facts was expensive and difficult – something only larger organizations could accomplish. Today, the advanced analytics needed to reconcile related entities over diverse data sets (commonly called Entity Resolution) on a Big Data scale are becoming available to organizations of all sizes. As more data, from more sources, assembles around a single individual, attempts to reliably protect individual identity are more easily compromised.8
The cost of a breach to an organization is not trivial. Research undertaken by the Ponemon Research Institute9 over the last decade shows that the cost to an organization is in the million dollar plus range, with the average number of records breached at just over 23'000. Extrapolate this to a Big Data environment and the consequences will be far more devastating because of the sheer number of individuals likely to be affected by a Big Data breach.
Indeed, an academic Ram Krishnan at the University of Texas at San Antonio recently noted at an NSF Workshop on Big Data that «Access control is one of the most powerful and fundamental ways of risk mitigation in any application. Interestingly, despite security concerns raised by Big Data applications, there is minimal research in this area.11
4.
Logical Access Control: Expressing Privacy and Context ^
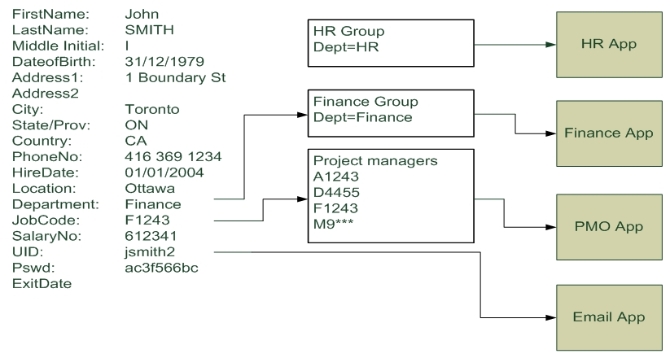
4.1.
The use of roles in establishing entitlements ^
4.1.1.
RBAC Example ^
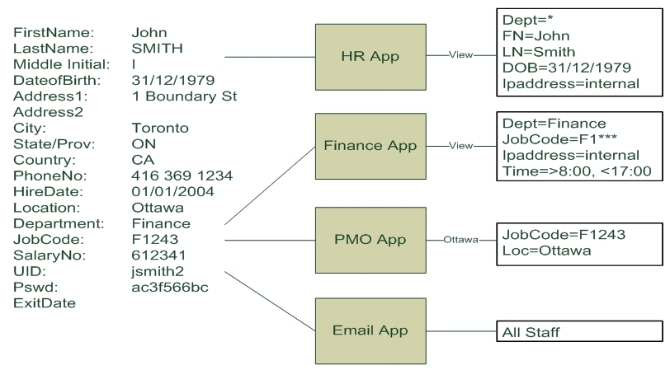
4.2.
The Attribute Approach ^
The system rules based on these attributes can also incorporate contextual privacy requirements that organizations are required to comply with under data protection laws such as:
- Restrictions on outsourcing personal data (e.g. several jurisdictions expressly prohibit personal data disclosure to a jurisdiction without similar privacy legislation).
- Data minimization where only personal data that is required for the provision of the requested product or service should be collected by an organization. It is not permissible to collect data that «might be» useful at some point in the future.
- Purpose specification that only allows an organization to use personal data for the express purpose for which it was collected, and where any secondary use requires the consent of the individual.17
4.2.1.
XACML - Data Loss Prevention ^
Preventing sensitive data from being read/modified by unauthorized users
Preventing sensitive data from being emailed to unauthorized users
Preventing sensitive data from being transferred via web-mail
Preventing sensitive data from being copied from one computer to another
Preventing sensitive data from being transferred to removable media
Preventing sensitive data from being transferred to disallowed URLs
4.2.2.
ABAC Example ^
There are various approaches to ABAC20 but they all rely on a rich data store of attributes generally aggregated from multiple authoritative sources. The core principle is to adhere to a published policy that determines the attributes required to gain access to protected resources.
- access decisions are centrally managed via policies rather than by individual application managers, which means that they are applied consistently across the organization, and administered by business managers rather than controlled by IT personnel;
- software development is simplified by the incorporation of «policy enforcement point» code which externalizes the access decision to a «policy decision point;»
- decisions are made at runtime based on attributes that may be combined to form fine-grained decisions; changes in access status are immediately recognized when attributes are updated.
4.3.
Industry Examples and Use Cases ^
Attribute based Access Control (Policy based Authorisation) is most applicable to those industries which are outlined below:
- Highly distributed with remote operating entities, perhaps in a subsidiary and parent environment, where these subsidiaries need to have on-line access to applications and services and where the principals are wanting to regulate subsidiary access and authorisation based upon a set of policies. Examples of these industries are:
- Financial Services sector
- Insurance sector
- Travel Agents
- Airlines
- Telecommunications companies in delivery of segmented services to clients
- Organisations that are mandated by government or regulatory policy to control what information is provided or what goods may be exported. Examples of these organisations are:
- Aerospace Manufacturers
- Defence Manufacturers
- Nuclear Energy Organisations
- Chemical Manufacturers
- Oil & Gas companies
- Exporters
- Customs Authorities
- Barrier Control organisations such as Meat Export, or Fruit Export organisations (Australian Quarantine & Inspection Service)
- Organisations that have a need for strong protection of their Intellectual Property and wish to protect that IP by the implementation of Policy Based Data Loss Prevention services. Examples would be:
- Pharmaceuticals companies
- Research & Development Organisations
- Organisations that have a requirement involving sensitive health data with associated consent management requirements. Examples in these cases would be:
- Hospitals
- Primary care (e.g. physicians)
- Secondary Healthcare Organisations
- Tertiary Healthcare Organisations
- Pharmacies
- Organisations that have a requirement to control access to Geospatial data and imagery and to share it using ABAC. This Imagery might be either highly classified or of more general nature for instance in disaster management; Examples of users would be:
- Emergency Management & First Responders
- Intelligence and Defence organisations such as the US defence Information Systems Agency, the German Federal Department of Defence and Australian Department of Defence, the US Geospatial Intelligence Organisation, the US National Security Agency (on Big Data projects such as the Ozone Widget Program) and agencies such as the Canadian, United Kingdom, Australian and NATO Defence Organisations.
- Statre & Federal Police Forces
- Government organisations that have a requirement to protect the data in their custody and control, which they share or distribute through the use of security classifications systems, where ABAC can be applied based upon the combination of document or Big Data security, the person seeking to have access to that data, any obligations required such as redacting portions of the document and other resource attributes and factors such as location, time of day, environment that need to be considered by the ABAC Policy servers when making the decision to allow or deny access.
4.3.1.
Government, Security and Classified Intelligence Documents ^
4.3.2.
Health Care ^
4.3.3.
Telecommunications Carriers ^
4.3.4.
Insurance ^
4.3.5.
Airlines ^
5.
Conclusion ^
6.
References ^
- European Commission. 2014. Progress On EU Data Protection Reform Now Irreversible Following European Parliament Vote. http://europa.eu/rapid/press-release_MEMO-14-186_en.htm.
- Federal Trade Commission (FTC). 2012. Protecting Consumer Privacy In An Era Of Rapid Change: Recommendations For Businesses And Policymakers. http://www.ftc.gov/news-events/press-releases/2012/03/ftc-issues-final-commission-report-protecting-consumer-privacy.
- «Privacy By Design Resolution». 2010. In 32Nd International Conference Of Data Protection And Privacy Commissioners. Jerusalem.
- Ten Tips For Reducing The Likelihood Of A Privacy Breach (Fact Sheet). 2014. Ottawa, Ontario: Office of the Privacy Commissioner, Canada. https://www.priv.gc.ca/resource/fs-fi/02_05_d_60_tips_e.asp.
7.
Privacy and Big Data Institute, Ryerson University ^
In the knowledge economy, the world is increasingly being mapped in vast sets of data points. With Big Data, information may be viewed as currency. Big Data is opening opportunities in business, medicine, education, city planning and development – virtually every sector of the economy.
Ryerson researchers in mathematics, science, engineering, commerce and more are studying Big Data in ways that affect business healthcare, public policy and everyday life. The institute will support this research, foster the growth of privacy-enhanced Big Data expertise and provide an educational platform through publications, panels, seminars, undergraduate and graduate course, continuing education programs and more.
The result will be a dynamic, multi-disciplinary, integrated experience at Ryerson powered by privacy-enhanced Big Data analytics and applications: tools, training, commercialization and adoption. The Privacy and Big Data Institute will direct those energies to address real-world issues.
Ann Cavoukian, Ph.D., Executive Director, Privacy and Big Data Institute, Ryerson University, Toronto, Canada. Ann.Cavoukian@ryerson.ca.
Michelle Chibba, M.A., Independent Privacy/Strategic Policy Expert, Toronto, Canada.
Graham Williams, BSC, MBA, Global Analyst, KuppingerCole and Director, KuppingerCole (Asia Pacific) Pte Ltd. gw@kuppingercole.com.
Andrew Ferguson, Industry Specialist in Identity and Access Management and Director, KuppingerCole (Asia Pacific) Pte Ltd. af@kuppingercole.com.
- 1 Glossary Of Key Information Security Terms. 2011. Washington, DC: National Institute of Standards and Technology (NIST). http://csrc.nist.gov/publications/nistir/ir7298-rev1/nistir-7298-revision1.pdf.
- 2 See also guidance provided by Canada’s Federal Privacy Commissioner’s Office. «Employees» access to personal information should be limited to what they need to know, particularly when this information is sensitive.» https://www.priv.gc.ca/resource/fs-fi/02_05_d_60_tips_e.asp.
- 3 Refer to the International Data Protection Commissioners» Resolution on Privacy by Design, October 2012 [http://bit.ly/1GSRvu4]; the U.S. Federal Trade Commission identification of Privacy by Design as one of three pillars for organizations in addressing consumer privacy [http://1.usa.gov/1DygKEC]; the EU draft privacy regulation that refers to taking a Privacy by Design approach to technology development [http://bit.ly/1wr1pAd].
- 4 Cavoukian, Ann. 2011. The 7 Foundational Principles. Implementation And Mapping of Fair Information Practices. Toronto: Information and Privacy Commissioner’s Office, Ontario. [http://bit.ly/1CqlWJa].
- 5 Cavoukian, Ann. Privacy and the Open Networked Enterprise. Information and Privacy Commissioner’s Office. December 2006.
- 6 Performance and Innovation Unit. 2002. Privacy And Data Sharing: The Way Forward For Public Services. UK Cabinet Office.
- 7 For further discussion on impact of Big Data on privacy, security and identity see for example, Cavoukian, Ann / Jonas, Jeff. Privacy by Design and Big Data. June 2012. Tene, Omer / Polonetsky, Jules. 2013. «Big Data For All: Privacy And User Control In The Age Of Analytics». Northwestern Journal Of Technology And Intellectual Property Vol 11 (Issue 5). http://scholarlycommons.law.northwestern.edu/njtip/vol11/iss. Richards, Neil M. / King, Jonathan H.. 2014. «Big Data Ethics». Wakeforest Law Review. http://papers.ssrn.com/sol3/papers.cfm?abstract_id=2384174.
- 8 Cavoukian, Ann / Jonas, Jeff. 2012. Privacy By Design In The Age Of Big Data. Toronto: Information and Privacy Commissioner’s Office, Ontario.
- 9 See Ponemon Institute / Symantec. 2013. Cost Of Data Breach Study: Global Analysis. Ponemon Institute..
- 10 Lafuente, Guillermo. 2014. «Big Data Security - Challenges And Solutions». Blog. https://www.mwrinfosecurity.com/articles/big-data-security---challenges-solutions/.
- 11 See Krishnan, Ram. 2014. «Access Control And Privacy Challenges In Big Data». Presentation, NSF Workshop on Big Data.
- 12 Frisch, Finn. 2014. The Identity And Access Management (R)Evolution: Federation And Attribute Based Access Control. Sweden: Axiomatics AB.
- 13 For more on this subject, see Kuppinger, Martin. 2015. «Identity Access Management». Blog. Adaptive Policy-Based Access Management (APAM): The Future Of Authentication And Authorization. https://blogs.kuppingercole.com/kuppinger/category/access-management/.
- 14 NIST An Introduction to Computer Security: The NIST Handbook, Special Publication 800-12. (Chapter 17 – Logical Access Control).
- 15 Nissenbaum, Helen. 2011. «A Contextual Approach To Privacy Online». Daedalus 140 (4): 32–48. doi:10.1162/daed_a_00113. See also Hart, Michael / Johnson, Rob / Stent, Amanda. 2013. «More Content – Less Control: Access Control In The Web 2.0». Academic Paper, Stonybrook University (Sunysb). http://spin2013.cs.sunysb.edu/~rob/papers/cbac-w2sp07.pdf.
- 16 See also discussion on «Adding Attributes to Role-Based Access Control» Kuhn, D. Richard / Coyne, Edward J. / Weil, Timothy R. 2010. «Adding Attributes To Role-Based Access Control». Computer 43 (6): 79–81. doi:10.1109/mc.2010.155. Merging the best features of RBAC and attribute-based systems can provide effective access control for distributed and rapidly changing applications.
- 17 Article 29 Data Protection Working Party. Statement of the WP29 on the impact of the development of Big Data on the protection of individuals with regard to the processing of their personal data in the EU. Adopted 16 September 2014. See also WP 29 Opinion 03/2013 on Purpose Limitation.
- 18 OASIS. eXtensible Access Control Markup Language (XACML) Version 3.0. January 2013. http://bit.ly/19x483Q.
- 19 There are a number of use cases for ABAC such as research undertaken by staff at MITRE Corporation. 2015. Scalable Access Controls For Lineage. McLean Virginia. Accessed February 17. https://www.usenix.org/legacy/event/tapp09/tech/full_papers/rosenthal/rosenthal.pdf. Rosenthal, Arnon / Seligman, Len / Chapman, Adriane / Blaustein, Barbara.
- 20 There is a an approach taken by e-Government Switzerland (e-CH 0107:IAM design principles) that defines the requirements, principles and rules that must be considered when deploying federated IAM solutions in eGovernment. The authors have been advised that this government standard describes an access mechanism that consists of a two-level granting of data access: the first level where widely accepted attributes are used; the second level where local attributes are used for fine-grained control. http://www.ech.ch/vechweb/page?p=dossier&documentNumber=eCH-0107&documentVersion=1.00.
- 21 Hu, Vincent C. / Ferraiolo, David / Kuhn, Rick / Schnitzer, Adam / Sandlin, Kenneth / Miller, Robert / Scarfone, Karen. Guide to Attribute Based Access Control (ABAC) Definition and Considerations. US Department of Commerce, NIST Special Publication 800-162 Guide to Attribute Based Access Control (ABAC): Definitions and Considerations. http://1.usa.gov/1aJynBD.
- 22 Ibid.
- 23 PHEMI. 2014. Balancing Access To Information While Preserving Privacy, Security And Governance In An Era Of Big Data. White Paper. Vancouver, B.C.: PHEMI. http://www.phemi.com/wp-content/uploads/2014/06/White-Paper-Privacy-Security-Governance-in-the-Era-of-Big-Data.pdf.
- 24 Cloud Security Alliance. Top Ten Big Data Security and Privacy Challenges. November 2012.