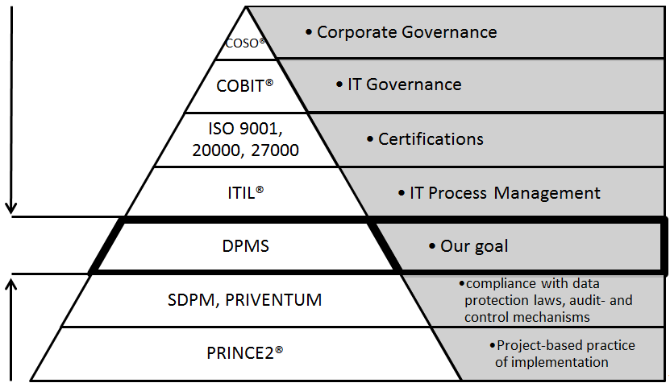
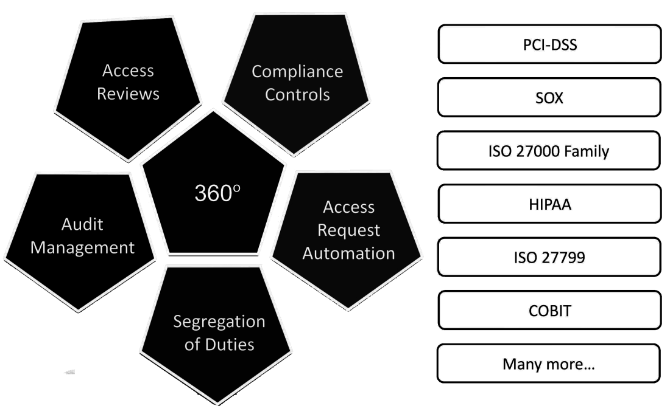
1.1.
Interdependences between Data Protection and Corporate Processes ^
1.2.1.
Personal Data, Information Lifecycle and Privacy by Design / Default principles ^
1.2.2.
Intellectual Capital ^
- Intellectual Capital – An advantage or asset that is developed from the use of notable mental capacity.
- Intellectual Property – A right or possession that is developed from the use of notable mental capacity.
1.2.3.
Conceptualization ^
1.3.
Business drivers for Data Governance ^
It is clear today that a crucial part of the organization business related digital information is unstructured data. Almost a decade ago Merrill-Lynch estimated that «More than 85 percent of all business information exists as unstructured data»3. Now, as business leaders realize that their data is exposed and out of control, immediate actions are required:
- Audit actual data access
- Map data owners, users groups and usage patterns
- Analyze the permissions of users and groups to data
- Recommend entitlement changes to meet business and regulatory policy
- Support user permissions review & grant process
2.1.
Supportive and opposing principles ^
2.2.
How to combine different approaches ^
3.
Achieving conformance with laws, guidelines and principles ^
3.1.
German Data Protection Law (BDSG) ^
| Goals | BDSG |
| Real-time Access Control | Ensure only authorized access to the systems where personal data is stored, processed or used (access control). |
| Governance | Ensure that proper access control to personal data is enforced during storage, processing, access or use (create, read, update, delete). |
| Security | Ensure that data is protected while «in motion» and being transmitted and cannot be viewed, changed or deleted without proper authorization. |
| 360 Degree Forensics | Ensure that you have the ability to establish and verify when and by whom personal data was entered into a computer system, as well as when and by whom this data was updated or removed. |
| Audit efficiency | Ensure and have audit trails to verify that personal data is Secured, stored, processed and transmitted in accordance with the instructions and approval of the principal (individual or entity referenced in the data). |
| Safe keeping | Ensure that personal data is protected against accidental destruction or loss (availability control) |
| Integrity | Processes to ensure the integrity of employees is protected |
| Access Management | Ensure user information is removed from Access systems when no longer valid |
4.1.
Define Unstructured Data ^
4.2.
Securing Unstructured Data ^
- Map existing stores of unstructured data.
- Find data (folders, files, sites) owners and map key user groups.
- Classify sensitive data.
- Define and enforce authorization policies on data stores.
4.3.
Structured & Unstructured Data Eco-Systems ^
4.4.
Requirements for an effective solution ^
The road to a complete solution that will provide actionable intelligence should contain the following milestones, at-least:
| Category | Requirement |
| Access Monitoring |
|
| Access Intelligence |
|
| Policy Compliance |
|
| Workflow |
|
5.
Conclusion ^
6.
Literatur ^
Blumberg, Robert Atre, Shaku, The Problem with Unstructured Data, http://secs.ceas.uc.edu/~mazlack/ECE.716.Sp2010/DM.Review.Unstructured.Data/DM.Review.Discovery.1.pdf, last revised 12 January 2015
Bock, Kirsten, Rost, Martin, Privacy by Design and the New Protection Goals – Principles, Goals, and Requirements. Published in German in: DuD 2011/01, https://www.european-privacy-seal.eu/results/articles/DuD2011-01-RostBock-PbD-NSZ.pdf/view
Gerick, T. (2012). IT Analytics. Wege aus der Black Box. Retrieved March, 9th, 2013 from http://www.manageit.de/Online-Artikel/20120910/f.%20IT%20Analytics.htm
Johnson, Eric, Symantec Global Internet Security Threat Report, Trends for 2009, http://eval.symantec.com/mktginfo/enterprise/white_papers/b-whitepaper_internet_security_threat_report_xv_04-2010.en-us.pdf, last revised 12 January 2015
Maseberg, Sönke, Die datenschutz cert GmbH stellt vor: priventum – das Zertifikat für das Datenschutz-Management, in: certNews, article of 5 August 2010, https://www.datenschutz-cert.de/news/cert-news/beitrag/browse/9/bp/474/artikel/die-datenschutz-cert-gmbh-stellt-vor-priventum-das-zertifikat-fuer-das-datenschutz-management.html, last revised 12 January 2015
Rost, Martin, Grundlagen des Standard-Datenschutzmodells (SDM), mit Anwendung auf auf BigData, https://www.datenschutzzentrum.de/sommerakademie/2013/IB10-Rost_SDM.pdf, last revised 12 January 2015
Waters, John, Whitepaper, Unstructured Data Governance, Holistic approach to key challenges, 2012
Philipp E. Fischer, Ph.D. cand. (UOC Barcelona), LL.M. in Intellectual Property Law (Queen Mary University of London / TU Dresden); Data Protection Officer & -Auditor (TÜV), Managing Partner at SuiGenerisData GmbH, Münchner Straße 18, 85774 Unterföhring, DE, pfischer@suigenerisdata.com, https://www.suigenerisdata.com
Ricardo Morte Ferrer, Ph.D. cand. (Zaragoza), Derechos Humanos y Libertades Fundamentales, Lawyer (Abogado), Master in Information and Knowledge Society (UOC), rmorte@arcor.de
- 1 Bock/Rost, Privacy by Design and the New Protection Goals – Principles, Goals, and Requirements. Retrieved March, 31st, 2013 from http://www.maroki.de/pub/privacy/BockRost_PbD_DPG_en_v1f.html.
- 2 Johnson, Symantec Global Internet Security Threat Report, Trends for 2009, http://eval.symantec.com/mktginfo/enterprise/white_papers/b-whitepaper_internet_security_threat_report_xv_04-2010.en-us.pdf, last revised 12 January 2015.
- 3 Blumberg/Atre, The Problem with Unstructured Data, http://secs.ceas.uc.edu/~mazlack/ECE.716.Sp2010/DM.Review.Unstructured.Data/DM.Review.Discovery.1.pdf, last revised 12 January 2015.
- 4 https://www.bsi.bund.de/EN/TheBSI/Functions/functions_node.html.
- 5 https://www.axelos.com/itil.
- 6 http://www.isaca.org/knowledge-Center/cobit/Pages/Overview.aspx.
- 7 Maseberg, Die datenschutz cert GmbH stellt vor: priventum – das Zertifikat für das Datenschutz-Management, in: certNews, article of 5 August 2010, https://www.datenschutz-cert.de/news/cert-news/beitrag/browse/9/bp/474/artikel/die-datenschutz-cert-gmbh-stellt-vor-priventum-das-zertifikat-fuer-das-datenschutz-management.html, last revised 12 January 2015.
- 8 Rost, Grundlagen des Standard-Datenschutzmodells (SDM), mit Anwendung auf BigData, https://www.datenschutzzentrum.de/sommerakademie/2013/IB10-Rost_SDM.pdf, last revised 12 January 2015.
- 9 http://www.gesetze-im-internet.de/englisch_bdsg/index.html.
- 10 Whitebox Security 2012, «WhiteOPs_Compliance overview».
- 11 Based on: Waters, Whitepaper, Unstructured Data Governance, Holistic approach to key challenges, 2012.