1.
Introduction ^
In this work, we focus on technical measures to protect the content and keep consumers honest by implementing a tracing ability to identify pirates who may have leaked protected material. There is no romantic notion attached to «pirates» (a coalition of dishonest consumers) that may perform attacks on the system. Our view is in terms of a game between a tracing authority and the pirates: false accusations must be avoided and pirates aim to disguise their identity when redistributing protected material. Identified traitors can be disconnected from further content transmissions and legal evidence of a pirate’s identity may deter potential traitors. Further notes on legal aspects can be found in the discussion section.
2.
Problem Statement ^
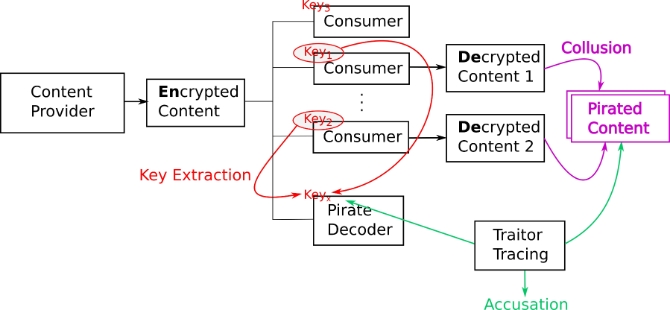
In Figure 1, we illustrate a basic broadcast encryption scenario where the content provider prepares encrypted content consisting of enabling blocks (EB) and cipher blocks (CB) and broadcasts it to its consumers, cf. [Prihandok 2013]. A subset of legitimate consumers will be able to decrypt the content protected (CB) by a session key which they derive by applying a set of personal keys [Chor/Fiat/Naor 1993]. To keep the session key s secret, it is split into shares s1, s2, …, sld N such that s=s1⊕s2⊕...⊕sld N where N is the number of possible consumers and ld denotes the base 2 logarithm. Each share sj is encrypted using two keys kj,0 and kj,1 so that the enabling block consists of 2·ld N subblocks. Each consumer is assigned a personal key Ki comprising a set of ld N keys: Ki={kj,b(i,j)} where b(i,j) is the jth bit of the binary representation of i. By using the personal key, a consumer can decrypt each share, either using the 0 or 1 key depending on the assignment, and then combine the shares to obtain the session key in order to unlock the cipher blocks. Note that only a subset of the kj,0 and kj,1 are revealed to each customer. Hence, a pirate decoder can only make use of the combined keys available to the traitors.
In this work, we focus on static (i.e. the key allocation is determined upfront) and symmetric broadcast encryption schemes. Since in symmetric schemes the secret is generated by the content provider and shared with the consumer, there is the problem of trust in the arbitration of disputes. This led to asymmetric broadcast encryption schemes that provide non-repudiation [Pfitzmann 1996].
3.
Countering the pirate decoder ^
Implementing cryptography (such as for the decoder in a broadcast encryption scheme) or content fingerprinting in an untrusted environment (such as the set-top box owned by a consumer) is hard. Secret key material may be extracted and DRM measurements may be bypassed after opening «the box» (which is mostly software) by means of reverse engineering and analysis. In this section, we review very recent results giving hope that tamper-resistant software may be possible and leading to reduced overhead for broadcast encryption. We caution that the discoveries do not immediately lead to practical code (yet), a lot more research is needed.
Encryption secures the communication between two endpoints. The problem in the broadcast encryption scenario is that the consumer endpoint is not an ideal black box, but its operation can be observed by a curious and sometimes malicious party. To improve security, tamper-resistant hardware can be employed, and physically unclonable functions (PUFs) [Maes/Verbauwhede 2010, Katzenbeisser et al. 2012] as a hardware-based one-way function can be used. Another approach is to turn to white-box cryptography [Wyseur 2009] in order to create a tamper-resistant program that can be safely executed in such an untrusted environment. A white-box cryptographic primitive can be observed, probed and executed but will not reveal the key embedded in the implementation. Careful definition of the security properties and the underlying assumptions aer paramount to the understanding. This field of research is called software obfuscation and deals with «encrypting functionalities» [Horváth 2015, Barak 2016]. Applications range from hiding a secret algorithm, secure software patching without disclosing the vulnerability being addressed, watermarking of software, backdoor functions, etc. Today, often heuristical obfuscators are used, relying on security by obscurity and secrecy, violating Kerckhoffs’s principle.
FHE allows to evaluate a function on ciphertext, such that the result is equivalent to the encryption of the function’s evaluation on the original plaintext. Partial homomorphic encryption, i.e. only supporting either addition or multiplication but not both, was known before. For privacy in cloud services, FHE is a crucial prerequisite as computation can be performed on the server side in an encrypted domain, without disclosing sensitive plaintext data. For the construction of iO, a primitive named cryptographic multilinear maps is used, also named «homomorphic quasi encryption» [Barak 2016]. In addition to the standard operations Enc, Dec, +, × there is a «comparison» operation Enc(x)≟Enc(y) which is true if x=y.
4.
Tracing pirate content ^
5.
Discussion ^
6.
References ^
Anderson, Ross, Copyright and DRM, Security Engineering, chapter 22, Wiley, 2nd edition, 2008.
Barak, Boaz/Goldreich, Oded/Impagliazzo, Russell/Rudich, Steven/Sahai, Amit/Vadhan, Salil/Yang, Ke, On the (im)possibility of obfuscating programs, Journal of the ACM, 59(2), 1–48, April 2012
Barak, Boaz, Hopes, fears, and software obfuscation: What does it mean to be secure? Communication of the ACM, 59(3):88–96, March 2016.
Bechtold, Stefan, From copyright to information law – implications of digital rights management. T. Sander, editor, Security and Privacy in Digital Rights Management, DRM ‘01, Lecture Notes in Computer Science, 2320, 213–232. Springer-Verlag, 2002.
Boneh, Dan/Shaw, James, Collusion-secure fingerprinting for digital data, IEEE Transaction on Information Theory, 44(5):1897–1905, September 1998.
Boneh, Dan/Shaw, James, Collusion-secure fingerprinting for digital data (extended abstract), Proceedings of the 15th Annual International Cryptology Conference on Advances in Cryptology, CRYPTO ‘95, 452–465, London, UK, 1995. Springer-Verlag.
Boneh, Dan/Sahai, Amit/Waters, Brent, Fully collusion resistant traitor tracing with short ciphertexts and private keys, Cryptology ePrint Archive, Report 2006/045, 2006. http://eprint.iacr.org/2006/045 (all Internet sources accessed on 31 January 2017).
Chor, Benny/Fiat, Amos/Naor, Moni, Tracing traitors, Proceedings of the International Cryptology Conference on Advances in Cryptology, Crypto ‘94, Lecture Notes in Computer Science, 839, 257–270. Springer-Verlag, 1994.
Cox, Ingemar/Miller, Mathew/Bloom, Jeffrey/Fridrich, Jessica/Kalker, Ton, Digital Watermarking and Steganography, Morgan-Kaufmann, 2nd edition, 2002.
Crosby, Scott/Goldberg, Ian/Johnson, Robert/Song, Dawn/Wagnerl, David, A cryptanalysis of the high-bandwidth digital content protection system. Security and Privacy in Digital Rights Management, Lecture Notes in Computer Science, 2320, 192–200, Springer, May 2002.
Danaher, Brett/Smith, Michael/Telang, Rahul, Copyright enforcement in the digital age: Empirical evidence and policy implications, Communications of the ACM, 60(2):68–75, February 2017.
Fiat, Amos/Naor, Moni, Broadcast encryption, Proceedings of the International Cryptology Conference on Advances in Cryptology, Crypto '93, Lecture Notes in Computer Science, 773, 480–491. Springer-Verlag, 1993.
Furon, Teddy, Watermarking security, Information hiding, chapter 6, Artech House, 2016.
Garg, Sanjam/Gentry, Craig/Halevi, Shai/Raykova, Marianna/Sahai, Amit/Waters, Brent, Candidate indistinguishability obfuscation and functional encryption for all circuit, Proceedings of the 2013 IEEE 54th Annual Symposium on Foundations of Computer Science, FOCS '13, 40–49, Berkeley, CA, USA, October 2013. IEEE.
Gentry, Craig, Fully homomorphic encryption using ideal lattices, Proceedings of the 41st Annual ACM Symposium on Theory of Computing, STOC '09, 169–178, Bethesa, MD, USA, May 2009.
Goldwasser, Shafi/Rothblum, Guy, On best-possible obfuscation, Proceedings of the 4th Conference on Theory of Cryptography, TCC '07, 194–213, Amsterdam, The Netherlands, February 2007. Springer.
González, Andés Guadamuz, Trouble with prime numbers: DeCSS, DVD and the protection of proprietary encryption tools, The Journal of Information, Law and Technology, 3, December 2002.
Henry, Kevin/Sui, Jiayuan/Zhong, Ge, An overview of the advanced access content system (AACS). Technical Report CACR 2007-25, Centre for Applied Cryptographic Research, University of Waterloo, Waterloo, Canada, 2007.
Horváth, Máté, Survey on cryptographic obfuscation. Cryptology ePrint Archive, Report 2015/412, 2015. http://eprint.iacr.org/2015/412.
Huang, Yen-Wei/Moulin, Pierre, One the saddle-point solution and the large-coalition asymptotics of fingerprinting games, IEEE Transactions on Information Forensics and Security, 7(1):160–175, February 2012.
Katzenbeisser, Stefan/Kocabaş, Ünal/Rožić, Vladimir/Sadeghi, Ahmad-Reza/Verbauwhede, Ingrid/Wachsmann, Christian. PUFs: Myth, fact or busted? a security evaluation of physically unclonable functions (PUFs) cast in silicon, Cryptology ePrint Archive, Report 2012/557, 2012. http://eprint.iacr.org/2012/557.
Maes, Roel/Verbauwhede, Ingrid, Physically unclonable functions: A study on the state of the art and future research directions, pages 3–37. Information Security and Cryptography. Springer, October 2010 .
Meerwald, Peter/Furon, Teddy, Toward practical joint decoding of binary Tardos fingerprinting codes, IEEE Transactions on Information Forensics and Security, 7(4):1168–1180, April 2012.
Naor, Dalit/Naor, Moni/Lotspiech, Jeffrey, Revocation and tracing schemes for stateless receivers. Advances in Cryptology, CRYPTO ‘01, Lecture Notes in Computer Science, 2139, 41–62. Springer, 2001.
Pfitzmann, Birgit, Trials of traced traitors, Proceedings of the First International Workshop on Information Hiding, Lecture Notes in Computer Science, 1174, 49–64, Cambridge, UK, May 1996. Springer.
Prihandok, Antonius/Ghodosi, Hossein/Litow, Bruce, A review on traitor tracing schemes, Technical report, James Cook University, Australia, September 2013. Available: https://www.researchgate.net/publication/256498106.
Qureshi, Amna/Rifà-Pous, Helena/Megı́as Jiménez, David, A survey on security, privacy and anonymity in legal distribution of copyrighted multimedia content over peer-to-peer networks, Technical report, Internet Interdisciplinary Institute, Universitat Oberta de Catalunya, Barcelona, Spain, September 2013. Working Paper Series DWP13-001.
Sahai, Amit, How to encrypt a functionality, Talk at the Quantum Games and Protocols Workshop, Simons Institute, University of California at Berkeley, February 2014, http://simons.berkeley.edu/talks/amit-sahai-2014-02-25.
Schaathun, Hans Georg, On watermarking/fingerprinting for copyright protection, Proceedings of the First International Conference on Innovative Computing, Information and Control, ICICIC ‘06, 3, pages 50–53, Beijing, China, August 2006.
Steinebach, Martin/Wolf, Patrick/Kim, Jee-Un/Engelhardt, Jens, Legal aspects of watermarking search services, A. Arnab, editor, Proceedings of the 8th International Workshop for Technical, Economic and Legal Aspects of Business Models for Virtual Goods: Incorporating the 6th International ODRL Workshop, 153–159, Namur, Belgium, September 2010.
Tang, Bo/Zhang, Jiapeng, Barriers to black-box constructions of traitor tracing system, Cryptology ePrint Archive, Report 2015/1070, 2015, http://eprint.iacr.org/2015/1070.
Tardos, Gabor, Optimal probabilistic fingerprint codes, Proceedings of the 35th Annual ACM Symposium on Theory of Computing, 116–125, San Diego, CA, USA, June 2003.
Tardos, Gabor, Optimal probabilistic fingerprint codes, Journal of the ACM, 55(2):1–24, May 2008.
Wyseur, Brecht, White-Box Cryptography, PhD thesis, Katholieke Universiteit Leuven, Belgium, March 2009.