1.
Introduction ^
[1]
This paper explores a person’s normative status that is entailed by a given situation. Therefore the theory of norms which was developed by Lachmayer (1977) is employed. However the present context is new. We concern the normative regulation of avatars in three-dimensional online virtual worlds1 (see Fig. 1). Hence, virtual worlds are viewed as an application domain.
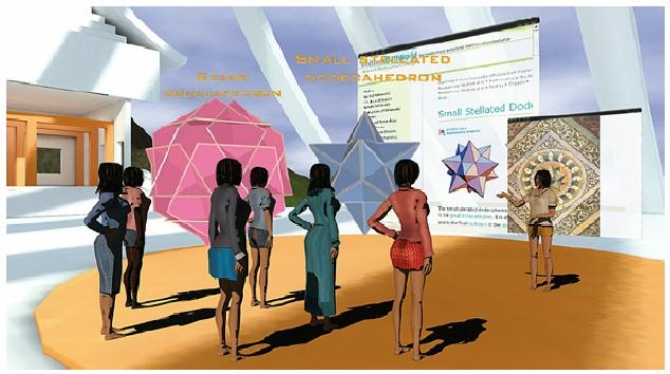
Fig. 1: Interacting with a complex 3D geometric object, dodecahedron, in the context of a geometry lesson within a virtual world [Čyras and Lapin 2010]
[2]
To explore the above mentioned issues, normative multiagent systems are reviewed. The norms and obligations of software agents have been investigated traditionally in informatics: computer science researchers proposing formalisms and programming languages for operationalisation of norms in software.
[3]
Sketching the legal issues of virtual worlds is first dealt in this paper. The metaphor of stage is employed here. Such a general sketch presents a personal reflection of the authors; it serves as visualization2 . It plays the role of a model, a symbolisation of the conceptual framework. It is generally called spatialisation.
[4]
Further the differences between the types of rules are addressed. Technical rules are impossible to violate, but legal rules (norms) can be violated.
[5]
All the rules are subject to implementation in virtual world software. In this context, law enforcement is a tough issue. The addressee concept of classical rules – persons – is supplemented with avatars. A sample «toy» rule ‹Keep off the grass› can illustrate constraints on avatar behaviour. Various methodologies are investigated worldwide to program the rules. Programming languages include external tools and script languages (e.g. LSL, Python, Lua, etc.). As a programming exercise, consider a virtual world and the following scenario. Suppose you build a house with a door which is controlled by a rule which permits entering avatars from a certain group only, e.g. your trusted friend avatars; other avatars are forbidden. In Second Life, this rule can be programmed by LSL (Linden Script Language). To program rules, each virtual world platform needs a specific framework.
[6]
The explored issues tackle the virtual world platform which is being developed within the VirtualLife3 project; see Section 3 for a fuller outline. Here the legal framework being constructed comprises a Virtual Constitution. The operational implementation of rules pays respect to Vázquez-Salceda et al. (2008).
[7]
A major part of this paper is devoted to formalising normative status. The notions of unified duty and summary duty are investigated. An example illustrates duties and permissions of a girl who sits in a cafe with her father.
[8]
In summary, this paper concerns structuring of legal semantics, in particular, duties and obligations.
2.
The Frame of a Virtual World ^
[9]
This section describes informally different kinds of rules in three dimensional virtual worlds that are inspired by a metaphor of architecture. Such an immersive virtual environment is different from 2D menu paradigm.
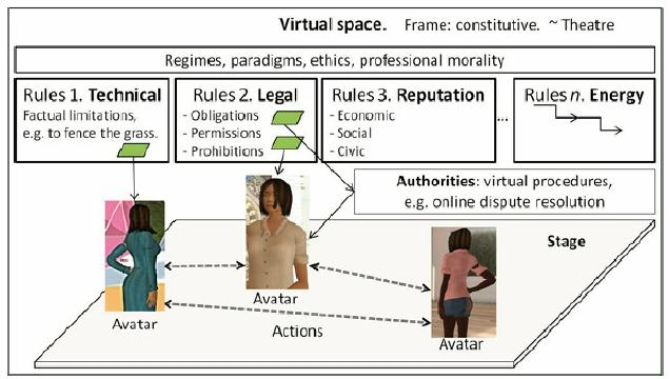
[10]
The frame – the reality of a virtual world – is constitutive. The entities are comprised of avatars, and 3D objects such as buildings, rooms, information stands, avatar inventories, etc. (see Fig. 1). An avatar is a computer user’s representation (usually a 3D model). Every avatar is monitored by its user. The avatar can also be viewed as the cursor on the screen.
[11]
The frame of a virtual world is established from the outset. A conceptualisation of the «theatre» is depicted in Fig. 2. The entities of major importance are avatars, their actions and rules, which regulate the behaviour. The avatars can also engage in joint actions. Avatar chat communication can be via voice or text chat.
[12]
Rules establish a regime (paradigm) of the virtual world. They can be divided into different classes such as technological rules (further – technical rules), legal rules, reputation rules, energy rules, professional rules, etc.:
[13]
Technical rules. They establish factual limitations. Real world examples are to fence the grass, to close the door to forbid entering, to refuse money by a cash machine if you do not provide the PIN code, etc. Violations are impossible: there is no possibility of violating a technical rule unless you break the artefact completely. Hence technical rules are strictly enforceable.
[14]
Legal rules. Their nature is that theycan be violated. For example, you can step the grass, you can take a train without a ticket, etc. But you risk being sanctioned. A procedure is enforced by an authority such as police, peacekeepers in a virtual world, etc. A sanction is imposed with a probability. Hence the legal rules are not strictly enforceable. Herein is the spirit of law. There is no strict boundary between technical and legal rules; a grey area exists.
[15]
The structural elements of legal rules are the same as of real-world norms. The subject is a natural person, a juridical person, etc. The modus is a deontic notion: obligatory, permitted, prohibited, etc.
[16]
Legal rules are of two kinds. The primary rules come first. Sanctions are determined by secondary rules. They are associated with authorities which enforce the rules. Virtual procedures can be raised for violations. For instance, online dispute resolution is a kind of procedure.
[17]
The modes of effect can be different. A sanction can be raised randomly with a certain probabilityp% . An example is a road rule which forbids crossing a street against traffic lights. You can go through a red light and if you are lucky a policeman will not punish you.
[18]
Legal rules are essential in virtual worlds – similarly as in the real world. It is impossible to implement normative regulation in a virtual world by means of technical rules only. Consider the norm that indecent content is forbidden in the virtual world. Such an abstract norm can hardly be implemented by automatic checking. For instance, a naked body need not be automatically treated as indecent content; this may be a picture of a statue in a virtual museum.
[19]
In VirtualLife a user agrees on a so called Virtual Constitution which consists of abstract legal rules. The Virtual Constitution is implemented as a click-wrap agreement. In this way it is part of End User License Agreement (EULA) and binds the users on the contractual level.
[20]
Energy rules. They sanction in the following way. If a prescribed behaviour is violated appropriate «energy» points are reduced. The addressee can be sanctioned effectively, i.e. 100%.
[21]
This can be illustrated by security/trust rules, reputation rules and the avatar identity card in VirtualLife. Each avatar has an ID card, which contains information about both his virtual and real life identities; see Fig. 3 [Bogdanov et al. 2009].
Fig. 3: Virtual identity card in VirtualLife [Bogdanov et al. 2009]. The reputation of avatars can be taken into account while chatting
[22]
The ID card includes simple indicators of trust. A red (entrusted) bar means that the avatar is a guest and has not proved his identity; a yellow (weakly trusted) bar – the avatar has an identity, but it has not been verified by any certification authority; and a green (trusted) bar – the avatar's identity has been verified by a certification authority. Each avatar also has an economic, social and civic reputation, whose indicators are handled by a sophisticated reputation system, depending on the avatar’s behaviour. Thus the rules are implemented in software by hard constraints.
[23]
Professional rules. Other kinds of rules comprise moral rules, user community rules, etc. Examples are provided further from the VirtualLife project where the users can engage in a trusted community called Virtual Nation. Different communities are governed by different rules. For instance, Students and Teachers form distinguished Virtual Nations in a University Virtual Campus that is purposed at learning support [Čyras and Lapin 2010].
[24]
The users are not absolutely free to agree on the community rules. Spindler et al. (2010) emphasize that the users cannot escape from the real world law.
[25]
Virtual Nation scenarios. A number of examples for allowing different scenarios can be proposed. Different values and rules are covered by NoCopy, CopyRight and CopyLeft nations4 . Permission language tables serve to implement distinguished rights. The permissions are represented explicitly in computer code.
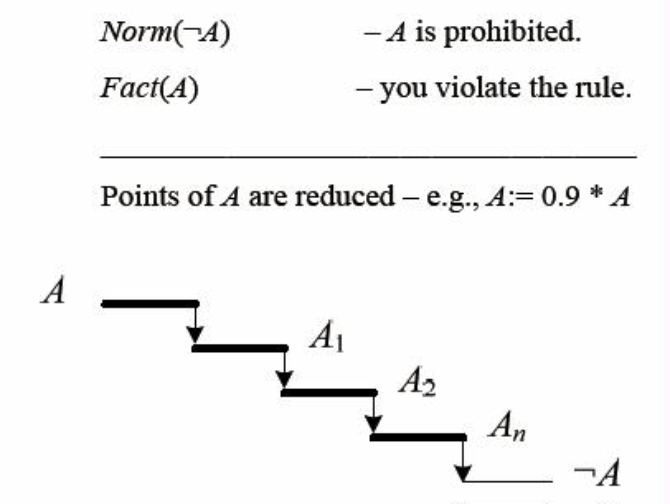
[26]
In a NoCopy nation, no one is allowed to make copies. In a strict copyright nation, only the author of the object can make copies. The receiver of the copied object cannot make copies.
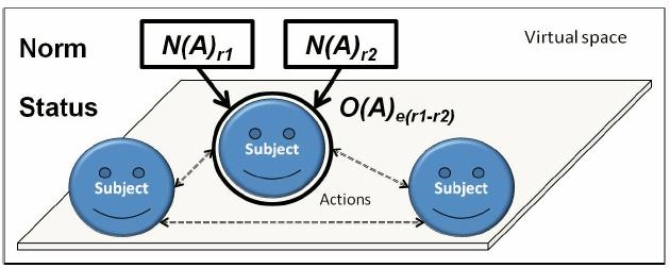
[27]
In a non-strict copyright nation, the original author of an object can decide if the new owner can copy the object or not. By default, an author or owner can copy.
[28]
In a CopyLeft nation, the creator’s information is preserved. Each user can change and copy its own objects.
[29]
In a Second Life model nation, you can sell objects controlling whether they are editable, copyable or sellable. The creator cannot modify a sold object. Of course, you can always move your own objects. For example, the seller can decide to sell non-copyable objects. This object cannot be duplicated by the new owner. Therefore if she puts them in her inventory they disappear from the world.
3.
Principles of Construction of a Virtual World Legal Framework ^
[30]
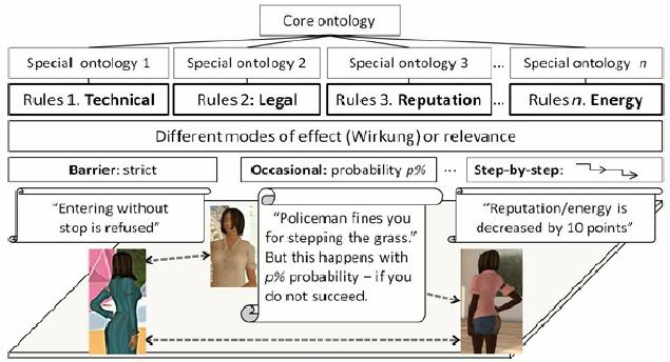
Rules can form different normative systems. Virtual world rules have different modes of effect or relevance, such as «barrier», «occasional», «step-by-step», etc. (see Fig. 4).
[31]
Barrier effect. A door is an example of a barrier technical rule. The technical rules are implemented with hard constraints. For implementation see Guideline 2 in Boella et al. (2009).
[32]
Occasional effect. The occasional type rule sanctions you with a certain probability. An example is a legal rule to buy the ticket when you take a train. However, you can succeed to travel without the ticket, but if a conductor does not sanction you.
[33]
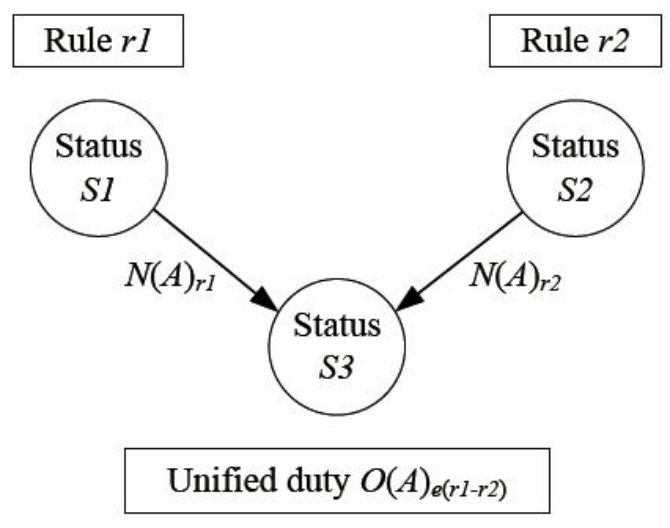
A dream of computer scientists (knowledge engineers) might be to implement the sanctions of each legal rule by means of technical rules. However this is against the spirit of law; see also the discussion of Philip Leith (2010).
[34]
Step-by-step effect. It is characteristic to reputation and energy rules. For example, each time you violate a rule, your points are decreased by 10%.
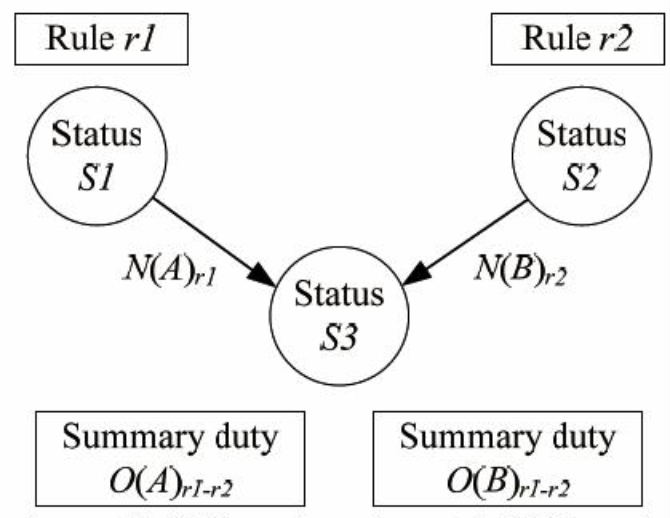
[35]
Ontologies. A core ontology is immanent within the whole set of rules. A special (material)domain ontologyi is present within each kind ofrulesi .
[36]
Technical filters. They can be set to enforce rules. For instance, in the context of e-law, legal texts can go through an XML filter. A document cannot be put on the «transport belt» of legislative workflow in case the document’s XML structure is flawed, e.g. marked-up with errors. Such a filter is an example of a technical rule. The ruling is of the type «Entering without stop is refused.»
3.1.
Three Legal Stages ^
[37]
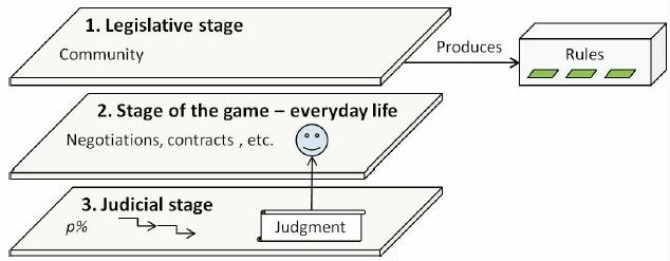
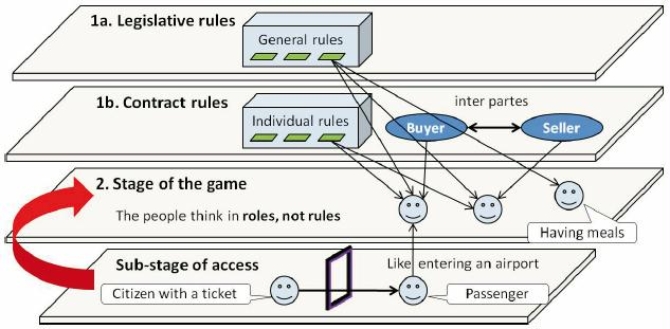
Three legal stages can be distinguished within a virtual world: (1) the legislative stage, (2) the negotiation stage – the stage of the game, and (3) the judicial stage; see Fig. 5. Their functions accord with the functions of law.
[38]
The legislative stage serves to produce rules. Here the whole in-world community can be involved. Next, the negotiation stage serves for everyday life. Social games including contracts are performed here. The judicial stage serves for judgments. This stage is not entered in each case. Distinguished modes of (virtual) legal proceedings are already identified above. Here activities such as story-telling, adjudication dialogs and legal disputes can be invoked.
[39]
The legislative stage consists of two sub-stages. On the first one, 1a in Fig. 6, legislative (general) rules are produced. It is compared with parliamentary activities, but performed by the community. On the second sub-stage, 1b, contract (individual) rules are produced.
[40]
A sub-stage of access can be distinguished within the stage of the game. It can be compared with an entering scenario. For example, in an airport a citizen with the valid ticket passes a procedure to become a passenger.
[41]
The people think in roles, not rules. In a virtual world, the concept of role is more important than the rule concept. In the real world people on the streets think in terms of roles. The people even do not know rules and paragraphs of the law. The first attempt to model the role concept is to put a label. Roles are widely employed in software; recall the roles of administrator, user, guest, etc. and distinguishing their access rights.
3.2.
Formalising Rules ^
[42]
The concept of technical rule is formalised in terms of necessity (a causal relationship). A legal rule is formalised as a formula in deontic logic; see among others, [Lachmayer 1977] and [Jones et al. 1992]. Energy rule prohibits certain behaviour; if violated addressee’s «energy points» are decreased.
[43]
A sketch, a kind of symbolisation, is below. Formalising normative systems, modelling legal argument and operational implementation of rules attracted a broad research of other authors; see e.g. [Prakken 1997], [Sartor 2007].
3.2.1.
Technical Rules ^
[44]
Technical rules are based on natural necessity (causation). They are formalised «IfP , thenQ ». In inference they can be employed with themodus ponens rule:
IfP , thenQ .
P .
ThereforeQ .
P .
ThereforeQ .
[45]
Or in the sequent notation,P →Q ,P |–Q . An example is the cash machine’s rule that is worded:
‹if PIN code is providedthen the cash machine gives money›
[46]
Formally:Rule (pin→money).
[47]
The idea of the rule is the entailment that in the case the PIN code is not provided, the cash machine gives no money, formally:
Rule (pin→money),Fact (¬pin) |–Fact (¬money)
[48]
It can be discussed whether the notation of the technical rule is «if and only if» (denoted iff or ↔):
‹if pin is providedthen cash machine gives money,and
if pin isnot providedthen cash machinedoes not give money›
if pin isnot providedthen cash machinedoes not give money›
[49]
Formally:Rule (pin↔money).
[50]
It should be noted that technical rules do not have the structural elementmodus . Therefore ‹ought› (obligatory) or ‹may› (permitted) is not included even in the grammatical formulation.
[51]
The technical rule concept can be viewed in the context of rule-based knowledge representation and compared with active rules in databases and business rules; cf. [Vasilecas et al. 2009].
3.2.2.
Legal Rules ^
[52]
Deontic status (e.g. obligatory, permitted, prohibited, etc.) is a structural element of legal rules. The nature of the legal rules is that a prescribed behaviour,Q , can be violated. Following is an example of an observed situation:
Obligation (P →Q ) – rule.
Fact (P ) – fact.
_______________________________
Fact (¬Q ) – observed violation fact.
Fact (P ) – fact.
_______________________________
Fact (¬Q ) – observed violation fact.
[53]
For example, the traffic lights rule permits you to cross only if the lights are green: ‹Permitted to cross iff green›. However, you can cross against the lights:
Permission (P ↔Q ) – cross only on green.
Fact (¬P ) – red is on.
___________________________________
Fact (Q ) – however you cross.
Fact (¬P ) – red is on.
___________________________________
Fact (Q ) – however you cross.
[54]
The observed behaviour is interpreted that you are simply a bad guy and nobody can stop you crossing.
[55]
Rule violations are sanctioned randomly with certain probabilities.
3.2.3.
Energy Rules ^
[56]
Energy (reputation, etc.) rules prohibit certain behaviour. Consider you violate a rule. Therefore, your energy points are reduced. Hence, you are sanctioned 100%. An example is as follows:
[57]
The interpretation is that your energy points are reduced toA1 , thenA2 and so on untilAn . At last the state ¬A is reached, which denotes no energy at all (Fig. 7). The shark fish is an example in the nature. A shark drowns if swallows too much.
4.
Normative Resultants ^
[58]
We view avatars as subjects to normative positions of virtual world rules (Fig. 8).
[59]
This section is devoted to formalise the concept of normative resultants of rules. Two concepts –unified status (einheitlicher Status) andsummary status (zusammenfassender Status) – are explored. Here we follow the theory of norms and the concept ofnormative resultants (normative Resultanten) [Lachmayer 1977, p. 88-92].
[60]
Consider a set of rules {r1 ,r2 ,…,rn }. Then different variants of normative status can be built. For simplicity a case of duties is analysed below. Hence, the normative status of the addressee’s duties is concerned.
[61]
Denotations. The structural elements of rule are the same in both the real and a virtual world. The essential elements of a rule,r , are denoted as follows:
1. ConditionCON . Denoted bycondition (r )
2. Disposition
2. Disposition
a. subjectSUB . It is denoted bysubject (r ). This is the addressee;
b. actionA . It is denoted byaction (r );
c. normative modus (obligatio ,permissio , etc.). It is denoted by
modus (r );
d. objectOBJ . It is denoted byobject (r ).
3. Sanction. It is established by a secondary rule.b. actionA . It is denoted byaction (r );
c. normative modus (obligatio ,permissio , etc.). It is denoted by
modus (r );
d. objectOBJ . It is denoted byobject (r ).
[62]
Hence the rule,r , is constructed of its elements:
r := (condition=CON ,subject=SUB ,action=A ,modus=MOD ,
object=OBJ , … )
object=OBJ , … )
[63]
The constructor ofr is denoted for short byr = (CON ,SUB ,A ,MOD ,OBJ ).
[64]
The existence (validity) of the rule is denoted by a predicateN :
N (condition=CON ,subject=SUB ,action=A ,modus=MOD ,object=OBJ )
[65]
This is also denoted byN (A )r orN (A ) – to stress the behaviourA .
[66]
In virtual worlds the subject concept is extended. Apart of natural persons and juridical persons, the subject comprises avatars. Hence, in the case of technical rules, the addressee is extended to real/virtual world objects such as cash machines, doors, houses, geometrical bodies (cubes, dodecahedrons), etc.
4.1.
Deontic Field ^
[67]
Relations between rule (norm) and the normative status of the duty have to be commented; see [Lachmayer 1977, p. 75-76]. Consider a normN (A ). The 4 cases can be created:
1.N (A ) – commandment (obligatory rule,Gebot );
2. ¬N (A ) – absence of commandment;
3. ¬N (¬A ) – absence of prohibition;
4.N (¬A ) – prohibition (prohibitive rule,Verbot ).
From each of the four cases above, a respective normative status is derived:
5.N (A ) →O (A ) – From commandment anobligatory duty arises (Aus dem Gebot ergibt sich einegebietende Pflicht ).
6. ¬N (A ) → ¬O (A ) – From the absence of commandmentno obligatory duty arises (Aus dem Mangel des Gebotes kannkeine gebietende Pflicht abgeleitet werden).
7. ¬N (¬A ) →¬O (¬A ) – From the absence of prohibitionno prohibitive duty arises (Liegt kein Verbot vor, so folgt darauskeine verbietende Pflicht ).
8.N (¬A ) →O (¬A ) – From prohibition aprohibitive duty arises (Liegt ein Verbot vor, so ergibt sich eineverbietende Pflicht ).
2. ¬N (A ) – absence of commandment;
3. ¬N (¬A ) – absence of prohibition;
4.N (¬A ) – prohibition (prohibitive rule,Verbot ).
From each of the four cases above, a respective normative status is derived:
5.N (A ) →O (A ) – From commandment anobligatory duty arises (Aus dem Gebot ergibt sich einegebietende Pflicht ).
6. ¬N (A ) → ¬O (A ) – From the absence of commandmentno obligatory duty arises (Aus dem Mangel des Gebotes kannkeine gebietende Pflicht abgeleitet werden).
7. ¬N (¬A ) →¬O (¬A ) – From the absence of prohibitionno prohibitive duty arises (Liegt kein Verbot vor, so folgt darauskeine verbietende Pflicht ).
8.N (¬A ) →O (¬A ) – From prohibition aprohibitive duty arises (Liegt ein Verbot vor, so ergibt sich eineverbietende Pflicht ).
[68]
The spirit of commandment and prohibition is expressed by 5 and 8 respectively.
4.2.
The Unified Status ^
[69]
The unified status (einheitlicher Status) is obtained when two (or more) variants of normative status have the same contents.
[70]
A simple example is of two rules,r1 andr2 . This means that the rules have (1) the same addressee and (2) the same action,A :
subject (r1 ) =subject (r2 )
action (r1 ) =action (r2 ) =A
action (r1 ) =action (r2 ) =A
[71]
As mentioned above, the contents are the same:contents (r1 ) =contents (r2 ).
[72]
The existence (validity) ofr1 andr2 is denoted respectively byN (A )r1 andN (A )r2 .5 The addressee is bound by two duties,O (A )r1 andO (A )r2 , which have the same contents.
[73]
A key question is «Can the two duties,O (A )r1 andO (A )r2 , of the same addressee be put together to form a normative resultant, which is called aunified duty and denoted byO (A )e(r1-r2) ?» The concept is depicted in Fig. 9.
[74]
The unified duty established byn rules {r1 ,r2 ,…,rn } is denoted byO (A )e(r1-r2-…-rn) or simplyO (A )e(1-2-…-n) . Each normri has the same condition, subject, action, etc. The construction of the unified duty brings a simplification. Separate duties and rules need not to be broken up. Instead of many duties, the sole unified duty is regarded.
[75]
An example of two rules is as follows. The first,r1 , is the road rule ‹Crossing the road on a red light is prohibited.› The second rule,r2 , is implemented with a technological devise – the traffic lights.
4.3.
The Summary Status ^
[76]
Consider two rules,r1 andr2 , with the same addressee,SUB , but different – though compatible – obligatory behaviours,A andB , respectively.
subject (r1 ) =subject (r2 ) =SUB
action (r1 ) =A
action (r2 ) =B
modus (r1 ) =modus (r2 ) = obligation
action (r1 ) =A
action (r2 ) =B
modus (r1 ) =modus (r2 ) = obligation
[77]
Though actionsA andB are different, the obligatory behaviour prescribed by the first rule,r1 , is compatible with the obligatory behaviour of the second rule,r2 . On the basis ofr1 , a dutyO (A )r1 arises. On the basis ofr2 , a dutyO (B )r2 arises. The second rule does not cover the obligatory behaviour of the first rule. Therefore the duty to doA does not arise fromr2 . Absence of this duty is denoted by ¬O (A )r2 .
[78]
Similar is valid for the first rule. Therefore the duty to doB does not arise fromr1 . Absence of this duty is denoted by ¬O (B )r1 .
[79]
In case only one rule – not both – is considered, the situation is as follows. On the basis of one obligatory rule, a duty arises. Here a question can be raised «Can both cases of normative status (duty, nonexistence of duty) be summed up in a normative resultant?» Such a normative resultant which sums different normative statuses up is called asummary status (zusammenfassender Status).
[80]
In the case of two rules,r1 andr2 , one duty and nonexistence of another duty lead to two variants. Thus two summary duties arise, actually, the first,O (A )r1-r2 , concerning the first obligatory behaviour, and the second,O (B )r1-r2 , concerning the second obligatory behaviour. The concept is depicted in Fig. 10.
[81]
In the case ofn rules,r1 ,r2 ,…,rn , consider a summary dutyO (X )r1-r2-…-rn . The index shows that the obligatory behaviour,X , is commanded by at least one rule,ri . The index does not show how many of suchri exist. One thing is for sure – not all the rules prescribe the sameX . Otherwise the unified duty is obtained. It is also true that no rule commands the opposite behaviour,¬X , which is incompatible withX .
[82]
The above example is built on two rules which lay down two different, though compatible, behaviours. How does the case of several rulesr1 ,r2 ,…,rn look?
[83]
LetAi denote the obligatory behaviour ofri . Consider rulesN (A1 )r1 ,…,N (An )rn . For eachAi of the compatible behaviours a summary duty can be established which is based on all the rules. A particular subset of rules induces a set of summary duties, which is equally large.
[84]
The construction of normative resultants is significant for the following reason. A behaviour prescribed by a separate rule is of little importance for the rule’s addressee, respectively the rule’s object. Instead, the behaviour which arises from the whole normative order is important.
[85]
Here the problem of rule contradictions can be tackled. Rules are produced by a certain subject (legislator). Therefore the rules can have contradictory contents. Science is not attributed the task to clean the contradictions. Science detects that the contradictions are available.
[86]
The task to clean contradictions can be assigned to certain authorities. Just some domains can be mentioned. Statutory rules are processed in legislative workflow. Software requirements are processed in software life cycle. Technical rules including those implemented in software are processed in software life cycle, too. Here the rules are verified, tested and validated.
[87]
A specification of a normative status synthesizer is as follows. Input is a list of rulesr1 ,r2 ,…,rn . Output is the normative resultantO (X )r1-r2-…-rn . Duties and permissions are in the focus.
[88]
In reality, the machinery and synthesis task requires human intelligence. A reason is that legal rules are formulated very abstractly. In the case of a big number of rules artificial intelligence techniques cope with complexity problems. Therefore, the first attempt to identify the resulting normative status is the concept of role.
4.4.
An Example of Normative Resultant: A Girl with her Father in a Café ^
[89]
Consider a situation – a girl with her father in a café. The girl’s normative status is represented as follows:
1. The father says «Sit down» → Obligatio to sit =O (A )r1
2. Implicit permission to speak → Permissio to speak =P (B )r2
3. A general prohibition to smoke in the café → Vetum to smokeV (C )r3 =O (¬C )r3
4. A specific prohibition to smoke for juvenile → Vetum to smokeV (C )r4 =O (¬C )r4
5. The father asks «What meals will you take?» → Permission for meals =P (D )r5
2. Implicit permission to speak → Permissio to speak =P (B )r2
3. A general prohibition to smoke in the café → Vetum to smokeV (C )r3 =O (¬C )r3
4. A specific prohibition to smoke for juvenile → Vetum to smokeV (C )r4 =O (¬C )r4
5. The father asks «What meals will you take?» → Permission for meals =P (D )r5
[90]
The normative resultant can be formalised as a list of all the five consequents from above:
O (A )r1 ,P (B )r2 ,O (¬C )r3 ,O (¬C )r4 ,P (D )r5 }
[91]
In further simplifications, indices can be omitted as rule numbers are of little importance for the addressee (the girl). Duplicated duties are abridged, henceO(¬C) will appear only once. The normative resultant is represented as the following list:
normative_resultantr1-r2-r3-r4-r5 = {O (A ),P (B ),O (¬C ),P (D ) } (1)
[92]
When interpreting the elements of the list, the commonsense understanding of duties and strong permissions has to be regarded. Duties are interpreted below with intersection. Therefore conjunction & is a connective in the formula:
dutiesr1-r2-r3-r4-r5 =O (A ) &O (¬C )
[93]
Permissions are interpreted with union. Therefore disjunction ( is a connective:
permissionsr1-r2-r3-r4-r5 =P (B ) (P (D )
[94]
In this example, duties and permissions,A ,B ,C andD , are viewed as being independent and no partial ordering is introduced.
[95]
Connecting the duties with conjunction and permissions with disjunction follows from deontic interpretation; see also [Sartor 2007, p. 453-497]. In the case of duties with conflicting actions, such as {O (goNorth ),O (goSouth )}, the smallest duty, their intersectionO (goNorth ) &O (goSouth ), results. In the case of permissions with conflicting actions, such as {P (goNorth ),P (goSouth )}, the largest permission, their unionP (goNorth ) (P (goSouth ), results.
[96]
Consider a one more permission for the girl – to take exclusively one soft drink:
6. The father asks «What one soft drink will you take, or cola (E1 ), or juice (E2 ), or water (E3 )?» → Permission for one soft drink =P (E1 )r6 xor P (E2 )r6 xor P (E3 )r6
[97]
The above permission is added to the normative resultant (1) above:
normative_resultantr1-r2-r3-r4-r5-r6 = {O (A ),P (B ),O (¬C ),P (D ), (P (E1 )xor P (E2 )xor P (E3 ) ) }
[98]
The normative resultant of the six rulesr1 ,…,r6 comprises permissions represented by the following formula:
permissionsr1-r2-r3-r4-r5-r6 =P (B ) (P (D ) ( ( P(E1)xor P(E2)xor P(E3) )
[99]
The interplay of obligations and strong permissions is studied by Boella and van der Torre (2008). They provide more elaborate examples in the context of hierarchies of authorities. They use Makinson’s and van der Torre’s framework of input/output logic [Makinson & van der Torre 2000]. The «Rex, Minister and Subject» game devised by Bulygin (1986) serves as an introduction.
4.5.
Incompatible Rules Result with ‹Impossible› Summary Obligation ^
[100]
In the case of incompatible obligatory actions, ‹impossible› summary duty results. In logic it is denoted by false, ( (bottom), or ( (empty). To illustrate consider a situation with two valid but incompatible rules:
text (r1 ) = ‹Save the mother›,text (r2 ) = ‹Save the child›
[101]
Conflicting actions mean an empty intersectionA ∩B =(. Formally, the set intersection of the operational implementations of the actionsA andB is empty:
operationalisations (A ) ∩operationalisations (B ) = (
[102]
Another example of hardly compatible rules is when the father says go (r1 ) and the mother says stay (r2 ). The resultant is a contradiction, go & ¬go. It is worth to note that the real world pragmatics forces the addressee (child) to sum the arising duties up to a middle behaviour like staying in the yard. Hence, other criteria sway which are not explicit in the rules, but implicit in the context.
4.6.
Synthesizing Normative Status ^
[103]
The problem of (semi-automatic) synthesis of normative status is formulated below. A specification of a normative status synthesizer can be formulated rather simply. Input is a list of rules,r1 ,r2 ,…,rn . Output is the normative resultant,O(X)r1-r2-…-rn ; see [Lachmayer 1977, p. 88-92]. This is depicted in Fig. 11.
Fig. 11: The input and output of a synthesizer of the normative status. The rulesr1 ,r2 ,…,rn serve as input. Output is the normative resultant of the rules
[104]
Implementation of the machinery is not an easy task. Synthesis of both duties and permissions is in the scope. In reality, the task requires human intelligence. A reason is that legal rules are usually formulated very abstractly. In the case of a big number of rules artificial intelligence faces complexity problems. Therefore, an attempt of identifying the resulting normative status is to assign a role, such as a passenger, a teacher, etc.
5.
Related Work ^
[105]
Multiagent Systems. Relevant formalisations are investigated by JURIX, DEON and Normative Multiagent Systems communities. Their formalisms are mathematically more precise than visualizations in this paper. Boella et al. (2009) introduce five guidelines for the use of normative systems in computer science; see also a whole volume devoted to agents and AI & Law. Boella et al. (2010) concern violations of legal rules and address goal-based interpretation and conflicting goals. Dignum et al. (2002) seek a long-term goal to extend the Belief – Desire – Intention (BDI) model, at a theoretical and practical level, with social concepts such as norms and obligations.
[106]
The obligation concept. With regard to the analysis of obligations, we have found useful the thesis of Adam Wyner (2008). He considers deontic logic as presented by Paul McNamara (2006) and provides linguistic considerations and natural language syntactic and semantic analysis. Wyner’s analysis of the Contrary-to-Duty Paradox (the Gentle Murder Paradox and the Good Samaritan Paradox) contributes to better understanding of obligations. The reader will understand the lexical semantics of obligations in case he finds mathematical axioms of deontic logic too heavy.
[107]
Virtual Institutions. Anton Bogdanovych’ (2007) work on non-game virtual worlds is very relevant. He developed the concept of Virtual Institutions (VI) «being a new class of Normative Virtual Worlds, that combine the strengths of 3D Virtual Worlds and Normative Multiagent Systems, in particular, Electronic Institutions [Esteva 2003].» Virtual Institutions are targeted at e-commerce. In Virtual Institutions an avatar is treated as an agent. The avatar can stop for a while interacting with its human master and continue independently as an agent that is governed by rules. Following is an example a rule: «Only participants with certain roles are permitted to enter particular rooms.» For instance, a Buyer is permitted to an Auction room but a Seller is prohibited.
[108]
Esteva (2003) sees Electronic Institutions as structures and mechanisms of social order and cooperation governing the behaviour of two or more individuals.
[109]
The ancient city of Uruk project [Bogdanovych et al. 2009] is interesting for the following reasons. Its specification is rather simple and consists only of a dozen abstract norms.
[110]
Virtual Institutions are defined as «3D virtual worlds with normative regulation of interactions» [Bogdanovych et al. 2007, p. 69]. A virtual institution is enabled by a three layered architecture. The Normative Control Layer employs AMELI to regulate the interactions between participants by enforcing the institutional rules. The Communication Layer causally connects the institution dimensions with the virtual world. The Visual Interaction Layer (supported by Second Life) visualizes the virtual world. Electronic Institutions technology brings the set of tools for formal specification of the institutional rules, formal verification of those and a system that controls the enforcement of these rules [Bogdanovych et al. 2009].
[111]
Law-Governed Interaction. The concept of ‹law› in VirtualLife differs from that in Law-Governed Interaction (LGI); see Naftaly Minsky (2005). LGI is a decentralized coordination and control mechanism for distributed systems – it can also be viewed as a «policy mechanism». The term «policy» is used for an informal statement of a set of rules-of-engagement, reserving the term «law» for a formalisation of this policy in a manner that can be enforced via LGI [Minsky 2007, p. 2]. LGI identifies two modes of law enforcement:
(a) by preventing violations of the given law;
(b) by reacting to violations.
(b) by reacting to violations.
[112]
LGI adopts the former stronger mode of law enforcement, (a). VirtualLife tackles both: the Virtual Constitution concept introduces the ‹soft› interpretation of rules; thus (a) is tackled. VirtualLife adopts (b) by reacting to violations. This is a case of the enforcement of rules which are created with the rule editor. Thus the ‹strong› interpretation of rules is adopted. Mode (a) is difficult to implement as punishment cannot be implemented in full scale in VirtualLife; mode (b) is easier.
[113]
The role of a lawL under LGI is to decide what should be done if a given evente occurs at an agentx operating under this law, when the control-state ofx iss . This decision, the ruling of the law, can be represented by the sequence of primitive operations mandated by the law, to be carried out, automatically, atx . More formally,L is a functionL :E (S →O* , whereE is a set of all possible regulated-events,S is a set of all possible states, andO is a set of all primitive operations [p. 8]. The event-condition-action rules have the form UPONevent IFcondition DOoperation-list . The rules are implemented in Prolog or Java. Thus, LGI rules are implemented as technical rules.
[114]
Computer code is law. The role of computer code in cyberspace can be compared with laws in real space.6 In particular, MMOGs (massively multiple online games) are also «determined by the code – the software, or architecture, that makes the MMOG space what it is» [Lessig 2006, p. 14]. Therefore the issues of the conception «code is law» are important. Software engineers have to regard limits of programming in regulation by code. Jurists have to regard limits of territorially based sovereigns.
6.
Conclusions ^
[115]
Virtual worlds are part of the real world. However legal and security virtual features need to be improved in order to guarantee safe and reliable virtual infrastructure. The paper reflects on this need and elaborates on possible solutions, including a legal framework. Formalisation issues are in the focus. Practical issues of virtual world law tackle governance in cyberspace and the concept of e-person, cf. [Schweighofer 2007].
[116]
In the approach worded «From rules in law to rules in artefact», we elaborate on an issue of regulation by computer code. The artefacts can be of different kinds. Additionally to embedded systems, the artefacts comprise software systems like virtual world platforms and virtual nations. Hence, the approach builds a bridge between law and informatics.
[117]
We aim to build a bridge between an Ought-to-Be reality and Is reality in the domain of virtual worlds. Here software developers identify the rules and implement them in computer code. A part of rules can be explicitly represented – the ‹strong› interpretation [Boella et al. 2007]. A part of rules cannot be represented explicitly. They are formulated explicitly in the system specification, namely, in the EULA text – the ‹weak› interpretation.
[118]
Modelling virtual worlds and implementing rules is a challenging task; not only for software developers. Therefore, the people think in roles, not rules. The names of roles, such as an author, an owner, a NoCopy nation, serve to describe situations. Formalisations and operational implementation require further research. This paper attempts to formalise normative status and thus contributes to structuring legal semantics.
[119]
Law enforcement in virtual worlds remains a tough problem. Legal rules are unfeasible to be programmed in the full extent in software.
[120]
We claim that the rule of law is required for both human and artificial agent communities. Different persons can pursue conflicting interests. Therefore the need arises for governance by rules. Operating systems perform the role of «arbiters» in communities of computer programs that compete for common resources. Similarly, the behaviour of agents (avatars) in virtual worlds has to be regulated by rules that constitute the law of the virtual world.
7.
References ^
Bogdanov, D., Crispino, M.V., Čyras, V., Glass K., Lapin, K., Panebarco, M., Todesco G.M., Zuliani F., VirtualLife virtual world platform: peer-to-peer, security and rule of law. In: eBook Proceedings of 2009 NEM Summit Towards Future Media Internet, Saint-Malo, France, 28-30 September, pp. 124-129, Eurescom GmbH (2009).
Bogdanovych, A., Virtual Institutions. PhD thesis, University of Technology Sydney (2007)
Bogdanovych, A., Rodriguez, J.A., Simoff, S., Cohen, A., Sierra, C., Developing virtual heritage applications as normative multiagent systems. In: Proceedings of the Tenth International Workshop on Agent Oriented Software Engineering (AOSE 2009) at the Eight International Joint Conf. on Autonomous Agents and Multiagent Systems, AAMAS 2009, Budapest, Hungary, pp. 121-132 (2009).
Boella, G., Governatori, G., Rotolo, A., van der Torre, L., A formal study on legal compliance and interpretation. In: Proc. of the 13th International Workshop on Non-Monotonic Reasoning, NMR 2010, 14-16 May, Toronto (2010).
Boella, G., Pigozzi, G., van der Torre, L., Five guidelines for normative multiagent systems. In: Frontiers in Artificial Intelligence and Applications, vol. 205, Proceedings of the 2009 conference on Legal Knowledge and Information Systems, JURIX 2009, Governatori, G. (ed.), pp. 21-30, IOS Press, Amsterdam (2009).
Boella, G., van der Torre, L., Institutions with a hierarchy of authorities in distributed dynamic environments. Artificial Intelligence and Law 16(1), 53-71 (2008).
Čyras, V., Lapin, K., Learning support and legally ruled collaboration in the VirtualLife virtual world platform. In: Grundspenkis, J., Kirikova, M., Manolopoulos Y., & Novickis, L. (eds.) ADBIS 2009 Workshops, Proceedings of Associated Workshops and Doctoral Consortium of the 13th East-European Conference, Riga, Latvia, September 7-10, 2009. LNCS, vol. 5968, pp. 47-54. Springer, Heidelberg (2010).
Čyras, V., Glass, K., Zuliani, F., Transforming legal rules into virtual world rules: A case study in the VirtualLife platform. In: Schweighofer, E., Geist, A., & Staufer, I. (eds.) Globale Sicherheit und proaktiver Staat – Die Rolle der Rechtsinformatik. Tagungsband des 13. Internationalen Rechtsinformatik Symposions IRIS 2010, 25.-27. Februar 2010, Universität Salzburg, pp. 579-586. Österreichische Computer Gesellschaft (2010).
de Freitas, S., Serious Virtual Worlds: A Scoping Study. The Serious Games Institute, Coventry University Enterprises, JISC.www.jisc.ac.uk/media/ documents/publications/seriousvirtualworldsv1.pdf accessed 15. January 2011 (2008).
Dignum, F., Kinny, D., Sonenberg, L., From desires, obligations and norms to goals. Cognitive Science Quart., 2(3-4), 407-430 (2002).
Jones, A.J.I, Sergot, M., Deontic logic in the representation of law: Towards a methodology. Artificial Intelligence and Law, 1, 45-64 (1992).
Eppler, M.J., Burkhard, R.A., Knowledge visualization. In: Schwartz, D.G. (ed.) Encyclopedia of Knowledge Management. Idea Group Reference, Hershey, pp. 551–560 (2006).
Esteva, M., Electronic Institutions: From Specification to Development. PhD thesis, Institut d’Investigació en Intelligència Artificial (IIIA), Spain (2003).
Lachmayer, F., Grundzüge einer Normentheorie: Zur Struktur der Normen dargestellt am Beispiel des Rechtes. Duncker und Humblot, Berlin (1977).
Leith, P., The rise and fall of the legal expert system. In: European Journal of Law and Technology, vol. 1, no. 1 (2010).
Lessig, L. Code Version 2.0. Basic Books, New York (2006).
Makinson, D., van der Torre, L., Input-output logics. Journal of Philosophical Logic, 29(4), 383-408 (2000).
McNamara, P., Deontic logic. In: Gabbay, D., & Woods, J. (eds.), Handbook of the History of Logic, vol. 7, pp. 197-288. Elsevier (2006).
Minsky, N., Law-Governed Interaction (LGI): A Distributed Coordination and Control Mechanism. An Introduction, and a Reference Manual. Rutgers University.www.moses.rutgers.edu/documentation/manual.pdf accessed 14 . January 2011 (2005).
Prakken, H., Logical Tools for Modelling Legal Argument: A Study of Defeasible Reasoning in Law. Kluwer, Dordrecht (1997).
Sartor, G., Legal Reasoning: A Cognitive Approach to the Law. A Treatise of Legal Philosophy and General Jurisprudence, vol. 5. Springer, Heidelberg (2007)
Schweighofer, E., e-Governance in the information society. In: Schweighofer, E. (ed.) Legal Informatics and e-Governance as tools for the Knowledge Society, pp. 13–23. LEFIS Series 2.www.lefis.org/images/documents/outcomes/lefis_series/lefis_series_2/capitulo1.pdf accessed 15. January 2011 (2007).
Spindler, G., Anton, K., Wehage, J., Overview of the legal issues in virtual worlds. In: Daras, P., Mayora, O. (eds.) UCMedia 2009. LNICST, vol. 40, pp. 189–198. Springer, Heidelberg (2010).
Vasilecas, O., Kalibatiene, D., Guizzardi, G., Towards a formal method for transforming ontology axioms to application domain rules. Information Technology and Control, 38(4), 271–282 (2009).
Vázquez-Salceda, J., Aldewereld, H., Grossi, D., Dignum, F., From human regulations to regulated software agents behavior. Connecting the abstract declarative norms with the concrete operational implementation. Artificial Intelligence and Law, 16(1), 73-87 (2008).
Wyner, A., Violations and Fulfillments in the Formal Representation of Contracts. PhD thesis, King’s College London.www.wyner.info/research/Papers/ WynerPhDThesis2008.pdf accessed 15. January 2011 (2008)
Vytautas Čyras, Docent, Vilnius University, Faculty of Mathematics and Informatics, Naugarduko 24, 03225 Vilnius, LT,vytautas.cyras@mif.vu.lt ;www.mif.vu.lt/~cyras/
Friedrich Lachmayer, Professor, University of Innsbruck, Faculty of Law
Innrain 52, 6020 Innsbruck, AT,friedrich.lachmayer@uibk.ac.at ;www.legalvisualization.com/
This paper extends an article in the European Journal of Law and Technology (EJLT), vol. 1, no. 3, 2010,http://ejlt.org/ and a presentation at the British and Irish Law, Education and Technology Association conference BILETA 2010, 27-30 March 2010, Vienna. Section 4 «Normative Resultants» is new.
Bogdanovych, A., Virtual Institutions. PhD thesis, University of Technology Sydney (2007)
Bogdanovych, A., Rodriguez, J.A., Simoff, S., Cohen, A., Sierra, C., Developing virtual heritage applications as normative multiagent systems. In: Proceedings of the Tenth International Workshop on Agent Oriented Software Engineering (AOSE 2009) at the Eight International Joint Conf. on Autonomous Agents and Multiagent Systems, AAMAS 2009, Budapest, Hungary, pp. 121-132 (2009).
Boella, G., Governatori, G., Rotolo, A., van der Torre, L., A formal study on legal compliance and interpretation. In: Proc. of the 13th International Workshop on Non-Monotonic Reasoning, NMR 2010, 14-16 May, Toronto (2010).
Boella, G., Pigozzi, G., van der Torre, L., Five guidelines for normative multiagent systems. In: Frontiers in Artificial Intelligence and Applications, vol. 205, Proceedings of the 2009 conference on Legal Knowledge and Information Systems, JURIX 2009, Governatori, G. (ed.), pp. 21-30, IOS Press, Amsterdam (2009).
Boella, G., van der Torre, L., Institutions with a hierarchy of authorities in distributed dynamic environments. Artificial Intelligence and Law 16(1), 53-71 (2008).
Čyras, V., Lapin, K., Learning support and legally ruled collaboration in the VirtualLife virtual world platform. In: Grundspenkis, J., Kirikova, M., Manolopoulos Y., & Novickis, L. (eds.) ADBIS 2009 Workshops, Proceedings of Associated Workshops and Doctoral Consortium of the 13th East-European Conference, Riga, Latvia, September 7-10, 2009. LNCS, vol. 5968, pp. 47-54. Springer, Heidelberg (2010).
Čyras, V., Glass, K., Zuliani, F., Transforming legal rules into virtual world rules: A case study in the VirtualLife platform. In: Schweighofer, E., Geist, A., & Staufer, I. (eds.) Globale Sicherheit und proaktiver Staat – Die Rolle der Rechtsinformatik. Tagungsband des 13. Internationalen Rechtsinformatik Symposions IRIS 2010, 25.-27. Februar 2010, Universität Salzburg, pp. 579-586. Österreichische Computer Gesellschaft (2010).
de Freitas, S., Serious Virtual Worlds: A Scoping Study. The Serious Games Institute, Coventry University Enterprises, JISC.www.jisc.ac.uk/media/ documents/publications/seriousvirtualworldsv1.pdf accessed 15. January 2011 (2008).
Dignum, F., Kinny, D., Sonenberg, L., From desires, obligations and norms to goals. Cognitive Science Quart., 2(3-4), 407-430 (2002).
Jones, A.J.I, Sergot, M., Deontic logic in the representation of law: Towards a methodology. Artificial Intelligence and Law, 1, 45-64 (1992).
Eppler, M.J., Burkhard, R.A., Knowledge visualization. In: Schwartz, D.G. (ed.) Encyclopedia of Knowledge Management. Idea Group Reference, Hershey, pp. 551–560 (2006).
Esteva, M., Electronic Institutions: From Specification to Development. PhD thesis, Institut d’Investigació en Intelligència Artificial (IIIA), Spain (2003).
Lachmayer, F., Grundzüge einer Normentheorie: Zur Struktur der Normen dargestellt am Beispiel des Rechtes. Duncker und Humblot, Berlin (1977).
Leith, P., The rise and fall of the legal expert system. In: European Journal of Law and Technology, vol. 1, no. 1 (2010).
Lessig, L. Code Version 2.0. Basic Books, New York (2006).
Makinson, D., van der Torre, L., Input-output logics. Journal of Philosophical Logic, 29(4), 383-408 (2000).
McNamara, P., Deontic logic. In: Gabbay, D., & Woods, J. (eds.), Handbook of the History of Logic, vol. 7, pp. 197-288. Elsevier (2006).
Minsky, N., Law-Governed Interaction (LGI): A Distributed Coordination and Control Mechanism. An Introduction, and a Reference Manual. Rutgers University.www.moses.rutgers.edu/documentation/manual.pdf accessed 14 . January 2011 (2005).
Prakken, H., Logical Tools for Modelling Legal Argument: A Study of Defeasible Reasoning in Law. Kluwer, Dordrecht (1997).
Sartor, G., Legal Reasoning: A Cognitive Approach to the Law. A Treatise of Legal Philosophy and General Jurisprudence, vol. 5. Springer, Heidelberg (2007)
Schweighofer, E., e-Governance in the information society. In: Schweighofer, E. (ed.) Legal Informatics and e-Governance as tools for the Knowledge Society, pp. 13–23. LEFIS Series 2.www.lefis.org/images/documents/outcomes/lefis_series/lefis_series_2/capitulo1.pdf accessed 15. January 2011 (2007).
Spindler, G., Anton, K., Wehage, J., Overview of the legal issues in virtual worlds. In: Daras, P., Mayora, O. (eds.) UCMedia 2009. LNICST, vol. 40, pp. 189–198. Springer, Heidelberg (2010).
Vasilecas, O., Kalibatiene, D., Guizzardi, G., Towards a formal method for transforming ontology axioms to application domain rules. Information Technology and Control, 38(4), 271–282 (2009).
Vázquez-Salceda, J., Aldewereld, H., Grossi, D., Dignum, F., From human regulations to regulated software agents behavior. Connecting the abstract declarative norms with the concrete operational implementation. Artificial Intelligence and Law, 16(1), 73-87 (2008).
Wyner, A., Violations and Fulfillments in the Formal Representation of Contracts. PhD thesis, King’s College London.www.wyner.info/research/Papers/ WynerPhDThesis2008.pdf accessed 15. January 2011 (2008)
Vytautas Čyras, Docent, Vilnius University, Faculty of Mathematics and Informatics, Naugarduko 24, 03225 Vilnius, LT,vytautas.cyras@mif.vu.lt ;www.mif.vu.lt/~cyras/
Friedrich Lachmayer, Professor, University of Innsbruck, Faculty of Law
Innrain 52, 6020 Innsbruck, AT,friedrich.lachmayer@uibk.ac.at ;www.legalvisualization.com/
This paper extends an article in the European Journal of Law and Technology (EJLT), vol. 1, no. 3, 2010,http://ejlt.org/ and a presentation at the British and Irish Law, Education and Technology Association conference BILETA 2010, 27-30 March 2010, Vienna. Section 4 «Normative Resultants» is new.
- 1 Non-game virtual worlds such as Second Life, developed by Linden Lab,http://secondlife.com/ , are in the primary focus. About ‹serious› virtual worlds – opposed to leisure-based – see a scoping study by Sara de Freitas (2008).
- 2 Eppler and Burkhard (2006, p. 553) emphasize the role of visual cognition and perception and note that a majority of our brain’s activity deals with processing and analysing visual images: «If visualization is applied correctly, it dramatically increases our ability to think and communicate.»
- 3 VirtualLife project «Secure, Trusted and Legally Ruled Collaboration Environment in Virtual Life», 2008-2010, co-funded by EU FP7 ICT under DG INFSO Networked Media Systems,www.ict-virtuallife.eu .
- 4 The descriptions and designs in the virtual reality engine of VirtualLife software are mainly by Kevin Glass.
- 5 The notation in [Lachmayer 1977, p. 88] is followed.
- 6 «In real space, we recognize how laws regulate – through constitutions, statutes, and other legal codes. In cyberspace we must understand how a different ‹code› regulates – how the software and hardware (i.e., the ‹code› of cyberspace) that make cyberspace what it is also regulate cyberspace as it is.» [Lessig 2006, p. 5]